Microsoft Defender for Cloud Data Security — The Architecture of Trust

The New Epicenter of Security
In the modern enterprise, security has moved beyond firewalls and access lists — it now lives inside the data pipeline.
Every alert, every detection, every mitigation is powered by one foundational process: how a platform collects, processes, and protects data.
That’s what makes the latest Microsoft Defender for Cloud Data Security architecture so defining.
It isn’t just a blueprint for cloud defense — it’s a living architecture of trust.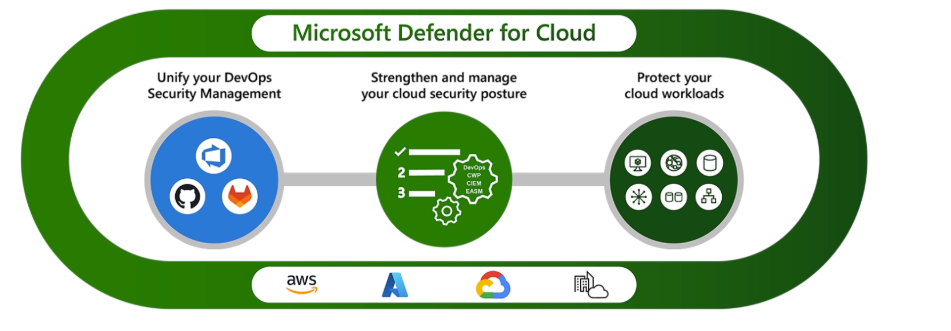
This new model shows how Microsoft has engineered a transparent, auditable, and privacy-aligned security fabric that prevents, detects, and responds to threats without ever compromising customer control.
Security, in this model, is not a reaction — it’s a designed outcome.
The Signal Foundation — The Cloud Security Graph
At the core of Defender for Cloud is an intelligent telemetry system: the Defender Security Graph.
It connects data from multiple sources across your cloud, network, and workloads — turning raw signals into correlated insight.
Four Pillars of Signal Intelligence
Azure Services:
Defender for Cloud continuously communicates with Azure resource providers to extract configuration states, policy compliance, and even AI prompt telemetry from Azure AI services.
This enables proactive detection of misconfigurations, identity risks, and data exposure in real time.
Network Traffic:
By sampling metadata — IPs, ports, protocols, and packet volume — Defender for Cloud detects anomalies and lateral movement across Azure’s backbone.
This lightweight model avoids deep-packet inspection, ensuring visibility without performance or privacy trade-offs.
Partner Integrations:
Defender for Cloud seamlessly ingests alerts from firewalls, SIEMs, and endpoint security tools — consolidating third-party intelligence into a single cloud posture.
Machine Telemetry:
Through Defender for Servers and Defender for Endpoint, Microsoft collects event logs, system behaviors, and OS-level telemetry from virtual machines and hybrid workloads.
Together, these signals form a real-time security graph — the analytic backbone for everything from Secure Score recommendations to AI-driven threat hunting.
“In modern security, the most powerful firewall is context — and Defender for Cloud captures it natively.” — Gaurav Agarwaal
Data Sharing — Intelligence in Motion
Security today is an ecosystem, not an island.
Defender for Cloud’s architecture embraces collaborative intelligence while keeping data ownership intact.
When malware scanning is enabled for Azure Storage, metadata such as file hashes (SHA-256) is securely shared with Microsoft Defender for Endpoint for multi-layer correlation.
Similarly, Cloud Security Posture Management (CSPM) data is exchanged with Microsoft Security Exposure Management, now in public preview, helping organizations quantify risk across identity, workload, and data surfaces.
Every exchange follows strict principles: only relevant metadata, used only for protection, always under the boundaries of privacy governance.
This is intelligence in motion — protection that moves with your data, but never beyond your control.
Data Protection by Design — Segregation, Access, and Governance
What stands out most in this architecture is how Microsoft treats trust as a system property, not a compliance checklist.
- Logical Segregation: Each customer’s data is logically isolated, tagged by tenant, and preserved with that identity throughout its lifecycle.
- Access Governance: Microsoft engineers can only access telemetry when necessary for investigations or recommendations, governed by the Microsoft Online Services Data Protection Addendum.
- Purpose-Limited Use: Customer data is never used for advertising, profiling, or model training — only to deliver and improve the service.
From a design standpoint, this is security by construction — not a bolt-on feature.
“True trust isn’t about encryption alone — it’s about intention built into architecture.”
— Gaurav Agarwaal
Data Use — Intelligence Without Exploitation
One of the most important design choices in Defender for Cloud is how Microsoft uses — and consciously limits — its use of data.
Instead of processing payloads, Microsoft analyzes patterns, not content, strengthening global threat intelligence while maintaining tenant confidentiality.
Moreover, Defender for Cloud does not train generative AI models on customer data unless explicitly authorized.
This is collective intelligence without compromise — shared defense, not shared data.
Data Collection — Customer-Controlled, Regionally Scoped
Data collection in Defender for Cloud is transparent and controllable.
When you enable protection, telemetry begins streaming across subscriptions — but the scope, region, and retention remain fully customer-defined.
Admins can manage collection in the Security Policy blade, disabling or narrowing telemetry for specific subscriptions as needed.
Even when collection is paused, key artifacts like VM snapshots remain available to maintain minimal defensive continuity.
Most importantly, data never leaves its region of origin.
Here’s how Microsoft aligns by geography:
| VM Geo | Workspace Geo |
| United States, Brazil, South Africa | United States |
| Canada | Canada |
| Europe (excluding UK) | Europe |
| United Kingdom | United Kingdom |
| Asia (excluding India, Japan, Korea, China) | Asia Pacific |
| India | India |
| Japan | Japan |
| China | China |
| Australia | Australia |
This alignment guarantees compliance with data residency and sovereignty laws — an essential requirement for global enterprises operating under GDPR and regional AI governance frameworks.
Data Consumption — From Signals to Situational Awareness
All that telemetry is only as valuable as its accessibility.
Defender for Cloud exposes its data streams through multiple channels, giving SOC teams direct access where they need it most:
| Stream | Data Types |
| Azure Activity Logs | Security alerts, just-in-time approvals |
| Azure Monitor Logs | Alerts and event telemetry |
| Azure Resource Graph | Compliance, recommendations, vulnerabilities |
| Defender for Cloud REST API | Security alerts, posture data |
Inactive data is automatically pruned after 30 days if no Defender plan is active — reinforcing privacy through minimalism.
Data Retention — Enough to Defend, Never to Hoard
Retention is a delicate balance between operational intelligence and privacy responsibility.
Microsoft draws this boundary with precision:
- Raw data: 14 days retention.
- Derived (calculated) data: an additional 14 days.
- AI threat protection telemetry: 30 days retention for anomaly detection.
Afterward, automatic deletion ensures the system retains only what’s essential for defense — nothing more.
This is ephemeral intelligence, not data accumulation.
Integration — The Unified Defense Fabric
Defender for Cloud doesn’t operate in isolation — it’s part of a larger defense ecosystem.
When any Defender plan is active, its telemetry seamlessly integrates with Microsoft Defender XDR (formerly Microsoft 365 Defender), merging cloud, endpoint, identity, and email signals.
The result is a cross-domain detection fabric that correlates events across vectors and stops multi-stage attacks faster than isolated tools ever could.
All shared telemetry adheres to the same security and retention standards defined across Microsoft 365 — one consistent trust model, one unified defense posture.
Architectural Takeaways — Security by Construction
The elegance of this architecture lies not in its complexity, but in its intentional simplicity.
Every design choice — data collection, segregation, and retention — reflects one guiding principle:
“The best defense is one that customers can audit, understand, and trust.” — Gaurav Agarwaal
This aligns perfectly with what I call the Five Pillars of Security Architecture for the AI Cloud:
- Transparency — clear, documented data flows.
- Granularity — customer control over collection and storage.
- Privacy Alignment — zero tolerance for repurposed data.
- Regional Compliance — full adherence to residency rules.
- Integration by Design — telemetry unified across domains.
Defender for Cloud embodies all five — turning security into a verifiable system of trust.
Closing Reflection — From Tools to Trust Systems
As cloud and AI continue to converge, our definition of security must evolve.
Tomorrow’s SOCs won’t just monitor events — they’ll govern trust systems capable of defending autonomously while staying accountable.
Microsoft Defender for Cloud is a blueprint for that evolution.
It demonstrates that powerful, proactive threat detection doesn’t require overcollection or opacity.
It’s a reminder that in this era of intelligent automation, data stewardship is the new security frontier — and Microsoft has designed an architecture that leads by principle, not by reaction.
“Security isn’t about seeing everything — it’s about seeing responsibly.” — Gaurav Agarwaal

Nice post
Nice Article