HealthCare 2026-2028 Trends : Winners Will Be Built on Logistics and Trust

Healthcare is entering a cycle where economics—not strategy decks—sets the operating model. The defining reality for 2026–2028 is sustained affordability pressure colliding with rising acuity and a workforce that cannot scale fast enough. Traditional levers (volume, rate, incremental cost cuts) are delivering diminishing returns; structural redesign is becoming mandatory.
What changed in the last 24–36 months is that rules and platforms are now rewriting business economics. Medicare Advantage is the clearest case study: the near-flat 2027 proposed payment update (~0.09%) signals a tighter regime where plans will be forced into repricing, benefit discipline, and deeper clinical and utilization-management rigor—because the growth-era slack is gone.
At the same time, healthcare is becoming a logistics business in new ways. Precision therapies (theranostics, cell and gene) turn time, temperature, and chain-of-custody into clinical outcomes and financial risk. Geopolitics is no longer background noise: the BIOSECURE Act (enacted December 18, 2025) constrains federal procurement and grants tied to designated biotech “companies of concern,” forcing boards to treat supplier exposure as an enterprise operating constraint—not a procurement optimization.
Finally, the platform layer is concentrating—raising both leverage and systemic risk. Interoperability is shifting from “integration projects” to utility operations (uptime, versioning, security, governance). TEFCA (Trusted Exchange Framework and Common Agreement) and its QHIN (Qualified Health Information Network) milestone signal that managed exchange is becoming a default expectation—raising the bar on data semantics, consent, identity, and resilience.
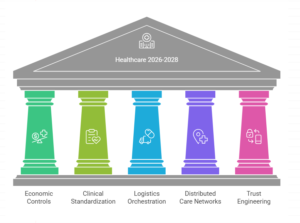
Where enterprises misread the moment: they treat GLP-1 coverage, MA remediation, site-of-care shift, supply-chain resilience, ambient/agentic automation, and interoperability as separate initiatives. They’re not. They are all expressions of one reality: healthcare is being re-platformed under affordability shock, policy volatility, workforce constraint, and board-level trust risk. The winners in 2026–2028 will operationalize this as one integrated system: economic controls, clinical standardization, logistics orchestration, distributed care networks, and trust engineering (governance + cyber resilience + uptime) as core capability.
Trend #1: GLP-1 & Metabolic Health Becomes a Permanent P&L Category (GLP-1 Economic Gravity Well)
In 2026–2028, GLP-1s stop being a “pharmacy spike” and become an enduring managed category that forces new benefit design, new clinical pathways, and new operating discipline. The organizations that treat this as a one-time coverage decision will get whiplash: utilization climbs, budgets break, and member friction rises. The organizations that win will treat metabolic health like a benefit platform with guardrails, wraparound care, and measurable outcomes.
The shift is already visible in how employers are responding. Instead of blanket coverage (or blanket exclusion), many are moving to clinically-driven eligibility pathways, requiring participation in lifestyle/behavior programs, and adding structured support for tapering/discontinuation—because persistence, drop-off, and rebound are now economic variables. (Omada Health Investors)
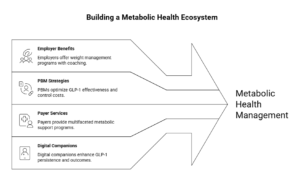
What’s already happening in the market (examples you can cite, non-hype)
- Employer pattern (Microsoft): Microsoft’s employee benefits include a Weight Management Program that combines coaching, nutrition guidance, and provider-supported medication management with an explicit “off-ramp” option—a concrete example of “metabolic platform,” not “drug coverage.” (usbenefits.microsoft.com)
- PBM pattern (CVS Caremark): CVS Caremark formalized a Weight Management program positioned explicitly as a way to optimize GLP-1 effectiveness and control costs; they also made formulary moves (e.g., excluding certain AOM brands from standard formularies) to force affordability and steerage. (CVS Health)
- Payer/PBM suite pattern (Optum Rx): Optum Rx’s Weight Engage frames the approach as medical-necessity standards plus wraparound support—again reinforcing “managed program” vs “open-ended scripts.” (business.optum.com)
- Payer services pattern (UnitedHealthcare): UnitedHealthcare positions Total Weight Support as a multifaceted program (not just a benefit toggle), aligning to the industry’s move toward bundled metabolic support. (UnitedHealthcare)
- Digital metabolic companions (Omada): Omada has pushed GLP-1 companion and prescribing support narratives tied to persistence and outcomes—signals of where employer-sponsored metabolic platforms are consolidating. (omadahealth.gcs-web.com)
Business impact: done well, this becomes a controllable category with predictable unit economics; done poorly, it becomes MLR volatility + member abrasion + governance risk as coverage decisions become visible and politicized. (SHRM)
CXO CTAs (tightened with “how to act”):
- Assign a single accountable owner for the metabolic P&L (not pharmacy) with outcome metrics: persistence, comorbidity improvement, downstream utilization, total cost impact. (SHRM)
- Implement Metabolic Guardrails: eligibility + participation requirements + continuation criteria (adherence/outcomes), so coverage scales through policy—not exceptions. (business.caremark.com)
- Build the off-ramp as a designed pathway (not ad hoc discontinuation). Microsoft’s approach is a useful reference point here. (usbenefits.microsoft.com)
- Treat formulary and program design as a price-and-access strategy, not a clinical-only decision (CVS formulary actions are a visible example of the new playbook). (business.caremark.com)
- Make member communication a trust asset: explain the “why” behind guardrails to reduce the perception of rationing. (SHRM)
Trend #2: The Medicare Advantage (MA) “Market Failure” Reset
MA is moving from a growth story to a margin-discipline regime—where payment math, Stars performance, coding integrity, and utilization control become the strategy. The reset isn’t theoretical: CMS’s(Centers for Medicare & Medicaid Services) CY 2027 Advance Notice projects a net average payment change of ~0.09% (about $700M) year-over-year if finalized, far below what the market had been pricing in, and it explicitly tightens payment accuracy levers.
The practical shift is that plans are being pushed into re-pricing, footprint discipline, and deeper clinical operating models. You can see the footprint story already in the 2026 landscape: UnitedHealthcare and Humana are exiting far more counties than they are entering (e.g., UHC exiting 225 counties; Humana exiting 198), reflecting the move from “everywhere growth” to “profitable geography and product focus.”
This trend exists because three pressures are compounding:
- Rate compression + payment accuracy changes (including CMS signaling policy changes that reduce the uplift from certain coding practices).
- Medical cost trend and higher utilization, forcing tighter benefit and UM design.
- Stars as economics, not just quality: Stars drives Quality Bonus Payments, and methodological shifts change plan economics faster than most operating models can adapt.
Business impact: MA becomes a “controls business.” Expect faster benefit redesign cycles, more aggressive utilization and network management, and higher sensitivity to Stars, coding, and audit readiness. Plans that can operationalize quality closure in-workflow, manage risk adjustment with compliance-grade rigor, and run utilization like an engineered system will defend margin; plans that can’t will cut benefits, exit counties, or accept earnings compression.
CXO CTAs:
- Stand up an MA Control Tower with one owner across Stars levers, coding integrity, UM, network, and member communications—because these are now one economic system.
- Treat Stars as weekly operations, not annual reporting: move closure into clinical workflows and contact-center journeys with accountable owners per measure.
- Pre-decide your footprint and benefit moves under constrained rate scenarios (base / downside): which counties/products you will defend, reprice, or exit—and what member messaging will preserve trust.
- Make coding and payment accuracy audit-ready by design (policy, tooling, sampling, escalation), not a scramble after denials or CMS scrutiny.
- Build “denial and prior-auth optics” into governance: the fastest way to lose brand and regulator attention is to optimize margin while eroding member experience.
Trend #3: “Payvidor” Consolidation 2.0 (The Walled Garden)
Payviders are entering a second phase of vertical integration where the goal is no longer “own more assets,” but run fewer seams. Consolidation 1.0 was strategy: acquire capabilities (payer, PBM, clinics, home, specialty, data). Consolidation 2.0 is operating discipline: prove the integrated stack produces measurable unit economics—lower total cost, higher retention, and higher quality—without triggering a trust discount from regulators, employers, and members.
The shift: from portfolio integration to journey internalization (“keepage”). The enterprise designs the end-to-end pathway and makes it executable: benefit rules → navigation → referral routing → site-of-care steerage → pharmacy fulfillment → adherence and follow-up. The point isn’t “closed networks.” The point is controlled execution in the places where healthcare bleeds money: missing handoffs, duplicated workups, out-of-network leakage, low-value utilization, and poor adherence.
The operational proof test (how integration actually wins): Integration only compounds when it reduces friction and leakage at scale—through a small set of repeatable controls:
- Leakage reduction: fewer referrals, scripts, and procedures escaping the network without clinical reason.
- Site-of-care discipline: ASCs, home infusion, virtual follow-ups, and lower-cost imaging become default when appropriate—enforced through routing rules, not “provider preference.”
- Medication economics control: specialty pathways, step therapy guardrails, formulary design, and adherence programs act as one system—not as separate payer and provider agendas.
- Administrative closure: eligibility, prior auth, care gaps, discharge follow-up, and denials don’t bounce between entities—one system owns closure.
The complexity tax (why many integrated plays fail): Most payvidors don’t fail because the thesis is wrong; they fail because they scale assets without unifying operations. You see it in four patterns:
- Duplicated operating layers: multiple care management teams, multiple navigation stacks, multiple “versions of truth.”
- Conflicted incentives: provider revenue optimization vs payer MLR control creates internal politics that slow decisions and increase friction.
- More handoffs, not fewer: integration can unintentionally add steps (more approvals, more policies, more queues) unless workflows are redesigned end-to-end.
- Member abrasion: steerage feels like denial when communication and transparency aren’t engineered; complaints and appeals become the visible tax.
Counterforce: antitrust and trust become design constraints, not afterthoughts. The integrated model will increasingly be judged not just on coordination claims, but on choice, pricing power, and fairness. That means payvidors must proactively build a defensible posture: clear conflict-of-interest governance, explainable routing, and member-first transparency—because the fastest way to lose permission to operate is to optimize margin while degrading experience or perceived choice.
Business impact: When executed well, Payvidor 2.0 becomes a compounding advantage: lower cost per journey, tighter utilization control, fewer avoidable ED visits/admissions, higher medication adherence, better quality scores, and higher retention. When executed poorly, it becomes the opposite: slower decisions, higher admin cost, worse member experience, provider abrasion, and rising regulatory heat—turning integration into a margin drag.
CXO CTAs (how leaders should respond):
- Pick 3–5 journeys to truly internalize (e.g., metabolic, oncology, renal, MS, complex chronic) and publish the end-to-end blueprint: routing rules, site-of-care standards, handoff ownership, and escalation paths.
- Instrument “keepage” as a managed KPI, not a slogan: leakage rate, steerage compliance, cost per journey, avoidable utilization, member friction (complaints/appeals), and retention—reviewed monthly like a P&L line.
- Build a conflict-of-interest governance model you can defend publicly: formulary decisions, referral routing, utilization management rules, and clinical appropriateness must be explainable, auditable, and consistently applied.
- Unify navigation + clinical programs + pharmacy operations into one operating cadence: shared work queues, shared exception handling, and shared outcome metrics—so the stack behaves like one system.
- Design the “choice + fairness” posture upfront: transparent member communication on why routing happens, easy escalation routes for exceptions, and monitoring for inequity or inappropriate denial-by-friction.
Trend #4: Value-Based Specialty Care (VBC 2.0) / Value-Based Risk Up the Acuity Curve
VBC is moving up-acuity—from primary care/shared savings into oncology, cardiology, renal, and other high-cost specialties where the real dollars sit. The shift is not “more VBC contracts.” It’s specialists taking accountable risk for episodes and longitudinal outcomes—forcing pathway control, cost visibility, and evidence-grade measurement as a condition of margin survival.
You can see the policy and market scaffolding forming. CMS (Centers for Medicare & Medicaid Services) continues to push specialty models—renal is the clearest signal: CMS’ own KCC (Kidney Care Choices Model) model update notes early quality gains (e.g., improved optimal starts, home dialysis, transplants) but net losses to Medicare in PY2023, which is exactly why the next wave of specialty risk gets stricter on economics, attribution, and performance mechanics. (Centers for Medicare & Medicaid Services) In parallel, kidney transplant access is being pushed through mandatory incentives in selected transplant hospitals (a sign that specialty value will increasingly be “designed” by policy, not negotiated ad hoc). (Avalere Health Advisory)
The operating reality of VBC 2.0 is that pathways become the product. Oncology and cardiology aren’t like primary care: comorbidities are dense, drug costs are volatile, and the “episode boundary” is hard. That’s why specialty VBC concentrates around: (1) guideline-concordant pathways, (2) avoidance of low-value utilization, (3) site-of-care discipline, and (4) tight measurement that can stand up to payer scrutiny. This is also why industry observers point to specialty risk as the next frontier—with large savings potential but high execution complexity. (McKinsey & Company)
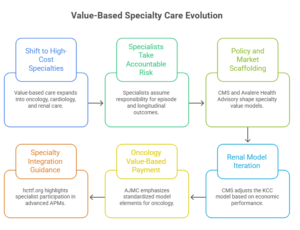
Concrete market signals worth referencing (without over-indexing on any one player):
- Renal: KCC policy and performance updates show CMS(Centers for Medicare & Medicaid Services) is willing to iterate the model when economics don’t work—even when quality improves—raising the bar on cost accounting and operational control in specialty risk. (Centers for Medicare & Medicaid Services)
- Oncology: Recent expert consensus work on oncology value-based payment emphasizes the need for clearly defined model elements that are feasible to implement—i.e., the market is standardizing what “good” looks like (measurement, accountability, patient-centered design). (AJMC)
- Specialty broadly: Specialty integration guidance highlights that specialist participation in advanced APMs is becoming meaningful (e.g., oncologists and nephrologists receiving bonuses tied to advanced APM thresholds), signaling that “specialty accountability” is no longer fringe. (hcttf.org)
Business impact: Specialty VBC will reallocate power toward organizations that can run repeatable pathways with proof: lower avoidable utilization, fewer complications, predictable episode economics, and documented outcome lift. It will also punish those who try to “contract into risk” without operational control—because drug mix, site-of-care, and variation will overwhelm the margin model.
CXO CTAs:
- Choose two specialties where you will take (or defend against) risk first, and define the unit economics: episode boundaries, drug cost exposure, site-of-care rules, and “avoidable utilization” targets. (McKinsey & Company)
- Build pathway governance with teeth: who owns the pathway, who can change it, how adherence is measured, and how exceptions are reviewed—because pathway drift is where risk contracts die. (AJMC)
- Stand up an evidence-grade measurement stack (outcomes + cost-to-outcome + equity lens) that can survive payer audit and supports outcomes-based contracting. (hcttf.org)
- Make specialty VBC a workflow program, not a reporting program: embed pathway nudges, site-of-care routing, and escalation rules into daily clinical operations. (Avalere Health Advisory)
- Decide your “risk posture” explicitly: where you’ll accept downside, where you’ll do shared savings only, and where you’ll stay FFS—but don’t let it be accidental or service-line political. (Centers for Medicare & Medicaid Services)
Trend #5: Zero-Based Clinical Costing (clean-sheet efficiency)
Under sustained inflation, providers are learning a hard truth: your biggest controllable margin lever is not “budgeting better”—it’s eliminating unwarranted variation with cost-to-outcome visibility. The next 24–36 months will reward systems that can price, measure, and standardize care at the pathway and clinician level—because cost pressures are “structural,” not cyclical, and traditional mitigation levers aren’t keeping pace.
The shift is from retrospective finance to clinical micro-economics: understanding the real unit cost of a case (including supplies, time, rework, LOS, complications), then using that transparency to drive standardization without degrading outcomes. This is where process mining and event-log analytics become practical weapons—because they expose the actual care path, bottlenecks, and rework loops, not the “intended” pathway in a policy binder.
A major accelerant is supply and device economics. Many systems are moving from “preference tolerance” to supply preference item governance and clinician-led standardization, because devices and supplies are rising cost centers and variation is often pure leakage. McKinsey’s work on supply costs emphasizes the need to engage physicians directly in supply decisions—because you can’t standardize from procurement alone. Evidence also suggests vendor rationalization can reduce expenditures without necessarily harming quality in specific contexts (e.g., single-vendor implant procurement studies).
Business impact: Zero-based clinical costing becomes the engine behind throughput (shorter LOS, fewer complications), labor efficiency (less rework and fewer handoffs), and purchasing power (standardized carts, implants, kits). Systems that operationalize it build a durable advantage: predictable service-line economics and higher reliability. Systems that don’t will keep “saving” money in spreadsheets while losing it in variation.
CXO CTAs:
- Pick 2–3 high-variance pathways (high volume or high cost) and publish a true cost-to-outcome view: clinician variance, LOS variance, supply variance, rework loops—then make it a standing ops review, not a one-time study.
- Stand up surgeon-to-surgeon variance transparency with a clinician-led governance model: what gets standardized, what remains preference, what requires evidence to justify exceptions.
- Make supply preference item governance real: tier products by clinical equivalence, standardize where evidence supports it, and measure savings plus outcomes (complications, returns to OR, readmissions).
- Use process mining to identify where “waste hides” (handoffs, delays, repeat labs/imaging, discharge friction), then redesign the workflow—not just the policy.
- Lock in a “clean-sheet” operating cadence: monthly pathway scorecards, quarterly playbook updates, and an exception process that is fast, documented, and measurable—so standardization improves instead of calcifying.
Trend #6: Theranostics & the “Just-in-Time” Nuclear Chain
Theranostics is turning parts of healthcare into a time-critical, exception-driven logistics business. The strategic shift is simple: when the “product” is a radioactive dose, time is inventory—and you can’t stockpile your way out of risk. Reactor downtime, production constraints, and distribution fragility translate directly into cancelled procedures and lost revenue, not just supply inconvenience.
The operational physics forces the new model. Key isotopes decay fast (e.g., technetium-99m has a ~6-hour half-life; fluorine-18 is ~110 minutes), which makes scheduling, transport, and last-mile handling part of clinical quality. Meanwhile, theranostic therapy isotopes like lutetium-177 have a longer half-life (~6.7 days), which enables broader distribution—but also expands the “nuclear chain” into a multi-node network with more handoffs to govern.
Why this trend exists now isn’t just growth in radioligand therapies—it’s that radiopharmaceuticals sit under two regulatory regimes at once: pharma GMP expectations and nuclear material rules. That dual compliance reality increases complexity in manufacturing, packaging, shipping, and site handling. And at the dispensing edge, “last mile” often runs through specialized nuclear pharmacy workflows where decay and geographic distance materially affect what can be prepared, repackaged, and administered.
Business impact: Theranostics will reward organizations that build a “dose control tower” mindset: orchestrated scheduling, chain-of-custody, and rapid exception handling (late delivery, failed QC, patient no-show, scanner delay, adverse reaction). Those who treat it like conventional drug distribution will experience preventable cancellations, wasted doses, and safety exposure—especially as volumes rise and supply tightness recurs.
CXO CTAs:
- Build a Theranostics Ops Control Tower: schedule + isotope availability + nuclear pharmacy prep + imaging suite capacity + staffing + transport in one operational view, with real-time exception queues.
- Standardize dose-level chain-of-custody: custody events, time stamps, QC checkpoints, and “stop conditions” that are enforceable across partners (sites, couriers, nuclear pharmacies).
- Engineer no-show and delay resilience: standby patient logic, reslotting rules, and escalation protocols—because decay makes cancellations uniquely expensive.
- Treat dual compliance as design input: align your QMS to satisfy both drug-quality and nuclear-material expectations; don’t bolt this on after scale.
- Contract for reliability, not just price: supplier diversification and uptime commitments matter because a single upstream disruption can cancel thousands of downstream appointments.
Trend #7: Cell & Gene as Logistics Businesses
Cell & gene therapy scaling is less a science problem than an orchestration problem. In autologous therapies especially, the product is patient-specific—so the “supply chain” is really a vein-to-vein workflow: collection → handoffs → manufacturing slots → QC release → cold-chain delivery → infusion scheduling. If any node fails, you don’t just lose inventory—you risk losing the patient window and burning six figures of value in one exception.
The shift in 2026–2028 is that winning programs will be built like air-traffic control for biology: chain-of-identity and chain-of-custody as first-class design, deterministic scheduling across apheresis and infusion, and exception playbooks for delays, product holds, and patient readiness. This isn’t optional polish—FDA expects sponsors to describe shipping/handling and chain of custody from manufacturer to clinical site as part of CMC expectations. (U.S. Food and Drug Administration)
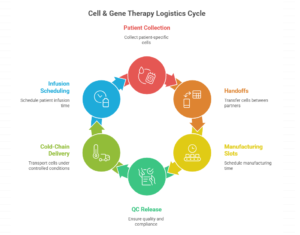
Why this trend exists now:
- Volume and commercialization are pushing programs beyond “hero ops.” Personalized therapies require patient-centered logistics across caregivers, clinical ops, and manufacturing partners—very different from linear pharma supply chains. (PwC)
- Identity and custody risk becomes existential: COI/COC are the safety rails that prevent mix-ups and support inspection readiness. (Standards Coordinating Body)
- Standards are hardening: the ISBT 128 Chain of Identity identifier is emerging as a practical way to standardize traceability across donations and manufacturing contexts, improving interoperability across the ecosystem. (ScienceDirect)
Business impact: Cell & gene becomes a competitive advantage for players who can reliably deliver on-time, compliant, and fully traceable therapy journeys. The upside is higher throughput per site, fewer failed handoffs, faster cycle times from referral to infusion, and fewer “lost slot” events that destroy both margin and patient trust. The downside of weak ops is brutal: cancellations, manufacturing waste, nonconformances, and regulatory exposure that slows scale.
CXO CTAs:
- Treat vein-to-vein as one owned process, not a handoff chain: assign a single accountable operator for scheduling, custody/identity, and exception resolution across partners. (PwC)
- Standardize COI/COC by design (not spreadsheets): unique identifiers, custody events, release gates, and verification at infusion—mapped to regulatory expectations for shipping/handling and chain-of-custody. (U.S. Food and Drug Administration)
- Build slot orchestration as a core capability: align apheresis capacity, manufacturing windows, QC release timing, and infusion chair availability so “schedule” becomes an engineered system. (PwC)
- Implement an exception playbook: product hold, courier delay, patient no-show, lab variance, temperature excursion—who decides, how fast, and what gets documented. (Standards Coordinating Body)
- Adopt or map to interoperable traceability standards (e.g., ISBT 128 CoI identifier) so scale doesn’t collapse into vendor-specific IDs and reconciliation work. (ScienceDirect)
Trend #8: Supply Chain & Logistics Re-enter as Competitive Advantage
Healthcare is rediscovering that supply chain isn’t “plumbing”—it’s differentiation and risk posture. As specialty volume grows and care shifts outside the hospital, the organizations that win will be the ones that can deliver reliability, compliance, and last-mile performance at scale. This isn’t about shaving pennies; it’s about preventing cancellations, avoiding shortages, and protecting continuity when disruptions hit.
The shift in 2026–2028 is from “efficient distribution” to resilient, automated, compliance-grade networks. In the U.S., distributors already move the majority of medicines (HDA cites ~95% through traditional channels), which means small improvements in DC automation, inventory precision, and exception handling compound into national-scale advantage. (Accelerator)
Two forces make this structural:
- Compliance becomes operational load-bearing. DSCSA’s (Drug Supply Chain Security Act) push toward interoperable, electronic traceability raises the bar on serialized handling, partner connectivity, and operational maturity—turning “can you execute traceability at scale?” into a competitive filter. (U.S. Food and Drug Administration)
- Specialty and home delivery are expanding the last mile. Direct-to-home supply models (e.g., diabetes and chronic supplies) and specialty distribution growth push logistics into the patient experience and adherence equation, not just B2B fulfillment. (Cardinal Health News & Media)
Market signals worth referencing:
- Network expansion + automation: Cardinal’s plan for a new automated distribution facility in Indianapolis (operational target: fall 2027) shows how the “warehouse” is becoming a strategic asset again—robotics and automated retrieval aren’t optional at scale. (Reuters)
- Automation as a throughput weapon: McKesson’s positioning of advanced automation in newer DCs reflects the industry move toward higher accuracy, faster cycles, and more resilient fulfillment. (mckesson.com)
- Specialty logistics investment is accelerating globally: DHL’s healthcare acquisitions (CryoPDP; SDS Rx) and its broader DHL Health Logistics investment thesis signal how much value is moving into cold chain and specialty courier capability. (DHL Group)
Business impact: The supply chain becomes a lever for revenue protection (fewer cancellations and stockouts), margin defense (lower waste, fewer expedites), and trust (consistent fulfillment, fewer “we can’t get it” failures). It also becomes a board-level risk topic because outages and third-party fragility now directly affect patient care and contracting leverage.
CXO CTAs:
- Treat distribution as a network product: define service levels (fill rate, on-time, cold-chain integrity), measure exception rates, and make reliability a first-class KPI—not a cost center metric. (Accelerator)
- Build a compliance-ready traceability posture (DSCSA :Drug Supply Chain Security Act and beyond): partner connectivity, audit-ready records, and operational playbooks for suspect/illegitimate product scenarios. (U.S. Food and Drug Administration)
- Invest in automation where it changes economics: robotic storage/retrieval, packing accuracy, and inventory intelligence—because the margin is in fewer touches and fewer errors. (Reuters)
- Industrialize last-mile specialty and home delivery: chain-of-custody events, delivery window precision, and proactive exception handling—so adherence and patient experience don’t collapse at scale. (Cardinal Health News & Media)
- Stress-test concentration risk: map tier-1 and tier-2 dependencies (3PLs, couriers, specialty hubs), then design continuity options before a disruption forces you into emergency procurement.
Trend #9: The “BIOSECURE” Supply Chain Reset
BIOSECURE changes the question from “is this supplier cost-effective?” to “is this supplier allowed?” In December 2025, a revised BIOSECURE framework became law (as Section 851 of the FY26 NDAA), introducing restrictions that can cut across federal procurement and federal funding when “biotechnology equipment or services” from designated biotechnology companies of concern (BCCs) are in the chain. (Arnold & Porter)
The shift in 2026–2028 is that geopolitics becomes an operating constraint: friend-shoring/dual sourcing, CDMO risk screening, and “supplier of concern” controls move from risk teams into the core of procurement, quality, and commercial planning. It’s not just about manufacturing; the scope can include sequencing platforms, software, and data services—i.e., areas where genomics and “multi-omic” data intersect with national security logic. (Sidley Austin)
Two details matter for operators (and they’re easy to miss):
- Designation + timelines are structural. OMB(Office of Management and Budget) is required to publish an initial BCC list within a year of enactment (by Dec 18, 2026), followed by implementing guidance and then FAR updates—meaning this is a multi-stage compliance program, not a one-time legal memo. (K&L Gates)
- The law was revised to be more “operable,” but not less consequential. For example, the reconciled text removed the earlier “has reason to believe” standard (easing some downstream visibility burden), yet the core economic reality remains: if a product/service becomes “tainted” under the framework, it can jeopardize eligibility for federal contracts/grants/loans tied to that supply chain. (Morrison Foerster)
Business impact: BIOSECURE drives near-term cost and timeline pressure (qualification and tech transfer aren’t fast), but the bigger impact is strategic: it forces compliance-grade supply chain design—where vendor selection, contracting clauses, and partner attestations become as important as price and capacity. It also changes M&A and partnering diligence: “who’s in your chain” becomes board-visible risk. (Baker McKenzie)
CXO CTAs:
- Build a BIOSECURE exposure map: which products, trials, platforms, and data flows touch federal contracts/grants/loans—then trace tier-1 and critical tier-2 biotech equipment/services dependencies. (Akin – Akin, an Elite Global Law Firm)
- Stand up BCC screening as a gate in procurement and partnering (CDMOs, CROs, sequencing, analytics, data services), tied to the DoD 1260H list and OMB (Office of Management and Budget) designation mechanics. (Baker McKenzie)
- Update contracts now: require attestations, right-to-audit language, substitution/transition obligations, and notification triggers if a supplier (or sub-supplier) becomes high risk or designated. (Morrison Foerster)
- Fund dual-source and tech-transfer readiness where switching costs are highest (late-stage programs, regulated manufacturing steps, core omics platforms). Treat this like resilience capex, not discretionary spend. (Goodwin Law Firm)
- Create an executive operating cadence (Legal + Procurement + Quality + Security + Commercial): monthly list/watch updates, scenario drills, and “decision rights” for when a dependency becomes unacceptable.
Trend #10: Distributed Care Networks—Ambulatory, Home, Hybrid (“Click-and-Mortar” Hybrid Care) — tightened
The next era of care delivery isn’t “telehealth versus in-person.” It’s network orchestration: routing patients to the right setting (ambulatory, retail, virtual, home, hospital) with consistent standards, reliable handoffs, and predictable unit economics. In 2026–2028, affordability and capacity will be won by systems that operate as multi-node networks, not hospital-centric enterprises.
The shift is already visible in utilization and build patterns: growth is concentrating in pre-acute outpatient settings (ASCs, urgent care) and expanding post-acute/home options—pushing the center of gravity for volume and margin outward. (McKinsey & Company)
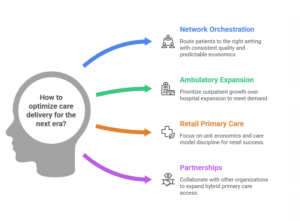
This trend exists because:
- Affordability shock forces site-of-care discipline: move appropriate care to lower-cost settings by default.
- Workforce constraint makes throughput a routing and standardization problem, not a staffing problem.
- Consumer expectations have matured: patients expect seamless movement from digital triage → appointment → follow-up without repeating the story. (Fierce Healthcare)
Market reality examples (signals, not slogans):
- Partnership-led hybrid access is scaling (e.g., Rush + Amazon One Medical) to extend primary care reach and specialty continuity. (American Hospital Association)
- Ambulatory footprint expansion is accelerating (e.g., CommonSpirit adding large numbers of ambulatory sites), reflecting a deliberate pivot toward outpatient growth. (Becker’s ASC)
- Retail primary care economics are tightening, so “owning sites” is less durable than “orchestrating journeys” (CVS/Oak Street; Walgreens/VillageMD). (Fierce Healthcare)
Business impact: Designed as a system, distributed networks reduce total cost via fewer avoidable ED visits/admissions, less out-of-network leakage, faster cycle times, and better retention. Without orchestration, they increase fragmentation—missed follow-ups, duplicated tests, medication drift, and dissatisfaction that reappears as avoidable utilization and complaint volume.
CXO CTAs:
- Define site-of-care as a routing system (criteria + rules + accountable owner), not a collection of sites. (McKinsey & Company)
- Build continuity-by-default: one longitudinal record, consistent triage standards, measurable handoff reliability across channels.
- Treat ambulatory expansion as an operating model rollout: standardized templates, staffing models, and service-line playbooks—not bespoke site launches. (Becker’s ASC)
- Make partnerships deliberate: partner for reach (hybrid primary care, navigation, retail access), own care standards, escalation protocols, and outcomes accountability. (American Hospital Association)
- Run the network on KPIs that matter: avoidable ED, leakage rate, time-to-next-available, handoff completion, no-show recovery, and total cost per attributed life—not channel vanity metrics.
Trend #11: Hospital-at-Home Industrialization (“The Great Repatriation”)
Hospital-at-home is moving from “innovative care model” to industrial operating capability—a virtual ward with real clinical accountability, logistics, escalation, and documentation that can scale beyond a pilot. The strategic shift is that acute capacity is increasingly created by repatriating appropriate inpatient days into the home—but only when the organization can run it like a system, not a program.
Two things are happening at once in 2026: momentum and policy fragility.
On momentum, leading programs are explicitly describing the model as command-center led with 24/7 access and coordinated in-home services (labs, IV therapies, imaging, med delivery). Mayo’s “Advanced Care at Home” makes the point plainly: patients are monitored remotely, supported by in-person services, and can reach the command center anytime—this is a clinical operations design, not “telehealth with a nurse visit.” (Mayo Clinic Health System)
On fragility, U.S. scale still depends on Medicare’s Acute Hospital Care at Home waiver environment—and that’s been living on short extensions. The waivers were set to expire January 30, 2026, and the House passed legislation in December 2025 to extend hospital-at-home waivers for five years (through 2030), but policy uncertainty remains a real operating constraint until the long-term path is settled. (Healthcare Dive)
Why this trend exists now:
- Affordability shock: inpatient capacity is expensive; avoidable bed-days are the most direct lever.
- Workforce constraint: home models can re-balance scarce inpatient staffing by shifting appropriate acuity to a different execution model (paramedics, virtual nursing, centralized physician coverage).
- Operational maturity is improving: CMS is publishing program data (signaling normalization and measurement expectations), which pushes programs from “storytelling” to comparative performance. (Centers for Medicare & Medicaid Services)
- Evidence is being debated in public: commentary around CMS’s evaluation highlights promising outcomes but also variability in readmissions and inconsistency in reporting—i.e., the next phase is standardization, not expansion-by-enthusiasm. (STAT)
Business impact: Done well, hospital-at-home converts inpatient throughput into a command-center asset: earlier discharge, better bed availability, improved patient experience, and lower total episode cost. Done poorly, it becomes a safety and reputation risk: inconsistent escalation, brittle vendor dependencies, documentation gaps, and “home is the new unit” without unit-grade controls.
CXO CTAs:
- Design it as a virtual ward, not a discharge program: standard eligibility, standardized clinical pathways, and “stop/transfer back” criteria with named medical leadership. (STAT)
- Build a 24/7 command center operating model with explicit roles: virtual RN coverage, physician escalation, paramedic/home-visit routing, pharmacy/lab logistics, and a single incident escalation path. (Mayo Clinic Health System)
- Treat home logistics as clinical quality: med delivery SLAs, device readiness, in-home service scheduling, and exception queues (no-show, delayed lab, device failure) with owners.
- Engineer policy resilience: plan for extension volatility (coverage, documentation, audit readiness) so the model survives regulatory whiplash. (JD Supra)
- Set outcome KPIs that prove “industrialization”: transfers back to hospital, adverse events, LOS impact, patient satisfaction, and net cost per case—tracked weekly with corrective actions.
Trend #12: The IoMT “Sensor Mesh” (Wearables as Vitals)
Wearables and remote monitoring are shifting from “more data” to clinical signal-to-action with accountability. In 2026–2028, the differentiator won’t be how many patients you enroll in RPM—it will be whether your organization can reliably detect vitals drift, route it to the right team, and close the loop fast enough to change outcomes without drowning clinicians in noise.
The shift is that wearables become prescribed sensing infrastructure, not consumer gadgets. That forces a different operating model: thresholds, escalation protocols, response SLAs, and documentation that stands up to audit and clinical scrutiny. CMS is already framing remote monitoring as a defined service with specific billing and documentation expectations across RPM/RTM, which pushes programs toward operational discipline (and away from “pilot dashboards”). (Centers for Medicare & Medicaid Services)
Why this trend exists now:
- Affordability + capacity pressure: you need early detection and fewer avoidable escalations, but you can’t add headcount to stare at feeds.
- Policy enables scale, but demands rigor: reimbursement exists, but it comes with requirements that reward standardized workflows over ad hoc monitoring. (Centers for Medicare & Medicaid Services)
- Device trust is now a first-order issue: FDA has emphasized limitations and accuracy considerations for common sensors like pulse oximeters (including labeling and performance expectations), which matters when you operationalize “sensor data as vitals.” (U.S. Food and Drug Administration)
- AI is pushing monitoring toward prediction: clinical literature is increasingly focused on turning continuous streams into actionable insights (not raw telemetry). (PMC)
Business impact: A true sensor mesh lowers total cost when it reduces avoidable utilization (ED visits, readmissions, decompensation events) and improves throughput via earlier intervention. But it can also backfire: noisy alerts create clinician fatigue, inconsistent escalation creates liability, and weak consent/data handling creates trust damage. The “mesh” only works when the enterprise owns the response system, not just the devices.
CXO CTAs:
- Define “signal-to-action” as the product: for each monitored condition, publish vitals drift thresholds, who receives the alert, required response time, and the escalation path (including when to route to virtual nursing vs physician vs ED). (Centers for Medicare & Medicaid Services)
- Create closed-loop accountability: every alert must end in a disposition (resolved/adjusted/escalated) with auditable documentation—otherwise you’ve built liability, not care. (Centers for Medicare & Medicaid Services)
- Tier devices by clinical risk and trust: align device selection and use-cases with FDA performance/labeling realities (especially for common sensors like SpO₂) so you don’t operationalize signals beyond their validated reliability. (U.S. Food and Drug Administration)
- Protect clinician capacity with an “alert budget”: design for high precision (fewer alerts, higher actionability), and staff a monitoring layer (pools/command center) so frontline clinicians receive exceptions—not continuous noise.
- Integrate into the longitudinal record intentionally: decide what becomes discrete chart data, what stays as summarized trends, and what must trigger tasks/orders—so the EHR becomes the action surface, not a passive archive.
Trend #13: The Conversational Experience Layer (Patient Voice Concierge + Clinician Voice UI)
The next “front door” in healthcare isn’t a portal refresh—it’s conversation as the operating surface for both patients and clinicians. In 2026–2028, the winning systems will treat conversational experiences as a single, governed layer that (1) resolves patient friction end-to-end (benefits, bills, scheduling, next steps) and (2) returns clinician capacity by making voice the fastest path to retrieve context, draft communications, and initiate routine workflow actions—without creating new safety or liability exposure.
What’s changing (and why it’s not incremental): Healthcare is finally turning the highest-friction moments into machine-executable journeys: explain → route → schedule → document → follow up. On the patient side, this is cost-to-serve math (deflection + conversion). On the clinician side, it’s throughput math (time returned + fewer clicks + faster closure). The shift is structural because the conversation layer can sit across channels (phone, portal, messaging, in-visit) and can be governed as a consistent “policy + workflow” system rather than a set of disconnected UI features.
Market signals you can cite (non-hype, in-workflow):
- Oracle Health announced new AI capabilities in its patient portal—patients can ask questions about their record, get plain-language explanations, draft messages, and schedule follow-up appointments, with general availability planned for 2026.
- Epic / Mayo Clinic shared real operational evidence: generative AI drafting of patient message responses to reduce nurse time per message (a concrete “in-basket load” lever, not a generic chatbot story).
- Microsoft Dragon Copilot is explicitly positioned as a unified voice AI assistant for clinical workflow—combining dictation, ambient capabilities, information retrieval, and workflow automation to reduce clinician administrative burden.
Why this trend exists now (healthcare-specific drivers):
- Affordability shock: contact centers and front-desk operations have become a cost-of-goods problem; reducing avoidable calls, confusion, and rework is direct margin defense.
- Workforce constraint: you cannot staff your way out of access, messaging, and documentation load; you must reduce friction per interaction.
- Trust and reputation risk: if the concierge explains coverage or next steps incorrectly—or voice triggers unsafe actions—errors become visible fast and scale quickly.
- Platform distribution: once the conversational layer is embedded in the EHR/portal and integrated into scheduling/messaging, adoption moves from pilots to defaults (and governance becomes non-negotiable).
Business impact: Done well, this becomes one of the highest-ROI levers in the stack: fewer inbound calls, higher appointment completion, fewer no-shows, faster message turnaround, reduced clinician “pajama time,” and better continuity because “next steps” are made explicit and executable. Done poorly, it becomes a trust hazard: confident misguidance, missed escalation, and inconsistent documentation—creating brand risk, safety risk, and complaint volume.
CXO CTAs (how leaders should respond):
- Unify patient + clinician conversation under one governed layer. Don’t let “patient chatbot,” “call center IVA,” and “clinician voice assistant” become separate stacks with separate policies and no shared escalation model.
- Define a Conversational Action Catalog (with autonomy tiers). What can the system explain vs do (schedule, draft, route, pend orders) and what always requires explicit human confirmation—especially anything that touches meds, orders, benefits determinations, or billing-sensitive actions.
- Instrument outcomes, not usage. Track first-contact resolution, call deflection, appointment conversion, message cycle time, rework rate, safety/complaint signals, and clinician time returned—by journey.
- Build escalation-by-design. Hard-code “when to hand off to a human” (clinical red flags, complex billing disputes, vulnerable populations, ambiguity thresholds) and make every escalation auditable.
- Treat the conversation layer as a trust product. Plain-language output, multilingual accessibility, disclosure norms, and error monitoring are part of the product spec—not compliance afterthoughts.
Trend #14: Ambient “Invisible” Documentation (The Death of the Keyboard)
Ambient documentation is becoming a license-to-operate capability for clinician capacity—but only if it’s treated as medical record production, not “note drafting.” The boundary matters: Trend #13 is the conversational experience layer (interface + navigation + action initiation); Trend #15 is the clinical record pipeline—ambient capture → structured note outputs → coding/quality artifacts → clinician QA loops—with controls that preserve accuracy, consent, and auditability. In 2026–2028, the killer KPI is no longer adoption; it’s time returned with record integrity preserved, measured by note latency, defect rates, and after-hours documentation reduction.
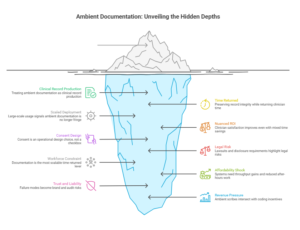
What’s already happening in the market (without reusing the Trend #14 vendor story):
- Scaled deployment signals it’s no longer fringe: The AMA has documented large-scale ambient scribe usage at The Permanente Medical Group (millions of uses) with reported reductions in documentation burden and meaningful “time back” outcomes. (American Medical Association)
- But ROI is not automatic: Reporting and studies increasingly show a nuanced reality—clinician satisfaction can improve even when hard time-savings are mixed, which means leaders must manage expectations and redesign workflows to capture throughput, not just “feel better” outcomes. (Axios)
- Consent is an operational design choice, not a checkbox: A 2025 JAMA Network Open study looked directly at consent processes for ambient documentation using generative AI—reinforcing that trust and disclosure mechanics are now part of implementation muscle. (JAMA Network)
- Legal risk is real and current: Reuters’ January 23, 2026 reporting highlights lawsuits and emerging state-level disclosure/review requirements, plus concerns about unauthorized recordings, vendor data handling, and hallucinations/omissions in the medical record. (Reuters)
Why this trend exists now:
- M3 Workforce constraint: documentation is the most scalable “time returned” lever available without hiring. (American Medical Association)
- M1 Affordability shock: systems need throughput gains and reduced after-hours work, but must prove quality doesn’t degrade. (JAMA Network)
- M4 Trust and liability: once ambient tools touch the legal medical record, the failure modes (omission, misattribution, hallucination, consent gaps) become brand and audit risks. (Reuters)
- Revenue/coding pressure is a hidden driver: emerging policy analysis notes ambient scribes intersect with coding incentives—so governance must explicitly separate “documentation quality” from “coding gamesmanship.” (Nature)
Business impact: Ambient documentation can deliver capacity and retention gains, but it also creates a new class of clinical safety and compliance obligations. Winners will treat ambient systems like regulated infrastructure: standardized prompts/templates, clinician verification loops, error monitoring, and consent discipline. Losers will deploy it as a productivity tool and then get surprised by record disputes, privacy complaints, and audit exposure. (Reuters)
CXO CTAs:
- Define “record integrity controls” up front: what must be verified by the clinician, how corrections are handled, and how omissions/hallucinations are detected and tracked as safety events—not IT tickets. (Reuters)
- Industrialize clinician QA loops: time-boxed review, structured edits, and feedback signals that improve templates and reduce repeated error modes.
- Standardize consent + disclosure as part of the visit workflow (and adapt by state/jurisdiction where required), with audit-ready evidence of consent. (JAMA Network)
- Separate productivity from reimbursement risk: establish documentation governance that explicitly addresses coding integrity and avoids creating incentives that won’t survive scrutiny. (Nature)
- Measure the right outcomes: after-hours “pajama time,” note latency, quality defects, rework rate, patient trust signals, and throughput—not just “minutes saved.” (JAMA Network)
Trend #15: Ambient and Agentic AI as the New Operating Layer
Ambient AI changes how work is captured. Agentic AI changes how work is executed. In 2026–2028, the competitive divide won’t be “who has copilots.” It will be who has a production-grade operating layer where agents can run multi-step workflows across systems—with exception queues, identity controls, and auditability engineered in.
The shift is from “task automation” to workflow execution: intake → validation → decisioning → action → documentation → follow-up, spanning EHR/claims/contact-center/authorizations and the messy middle where most cost sits. That’s why Gartner’s warning matters: they expect over 40% of agentic AI projects will be canceled by end-2027 due to cost, unclear value, and inadequate risk controls—meaning the bottleneck is operating discipline, not model capability. (Gartner)
Healthcare is already telegraphing where the operating layer will be applied first: administrative friction. For example, Humana’s plan to remove roughly one-third of prior authorization requirements and target one business day decisions for 95% of complete electronic prior auth requests reflects a market push toward faster, less burdensome admin workflows. (Reuters) Agents won’t replace policy choices like that—but they will become the mechanism that makes streamlined policy actually executable at scale.
Why this trend exists now:
- Affordability shock: admin cost-to-serve is too big to leave on human queues.
- Workforce constraint: capacity is created by removing touches and waiting, not hiring.
- Trust risk becomes board capital: once agents take actions, you must answer “who did what, on whose behalf, using what authority?”
- Control requirements are hardening: identity separation, least privilege, and clear audit trails are being explicitly called out as bedrock requirements for agentic systems. (OpenID Foundation)
Business impact: Expect meaningful cycle-time compression where processes are exception-heavy (prior auth, referrals, contact center, care management, claims operations). But the failure mode is equally clear: agent sprawl without a control plane yields permission drift, inconsistent approvals, and untraceable actions—exactly the conditions that create audit findings and reputational damage. The production requirement is observability: many enterprises still report agentic initiatives stuck at pilot stage, with security/compliance and operational visibility as major blockers. (IT Pro)
CXO CTAs:
- Mandate an Agent Minimum Control Standard for anything in production: agent identity, least privilege, tool access allowlists, approvals by risk tier, full audit logs, and rollback. No exceptions. (OpenID Foundation)
- Stand up exception-first operations: humans own the exception queues; agents handle the normal path. Measure: cycle time, rework rate, and “unowned exceptions.”
- Publish an enterprise Autonomy Ladder (assist → supervised → delegated) and make it enforceable via policy and permissions, not slideware. (Gartner)
- Build “prove it” telemetry: action traceability, error modes, drift, and incident response playbooks—so you can diagnose and contain failures fast. (IT Pro)
- Pick 3 workflows where waiting between steps is the bottleneck (e.g., prior auth status resolution, referral coordination, benefits clarification) and commit to outcome KPIs within a fixed window.
Trend #16: Agentic RCM (Autonomous Billing) — tightened
Revenue cycle management (RCM) is becoming an automation arms race—not because providers want it, but because denials, rework, and cash friction have crossed the threshold where humans can’t keep up. In 2026–2028, the shift is from “RCM optimization” to autonomous loops: coding → claim assembly → submission → denial prediction → appeal drafting → resubmission → A/R follow-up, with humans supervising exceptions and high-risk decisions.
The economics are already brutal: Premier estimated $25.7B spent by providers in 2023 contesting denials, with admin cost per denied claim rising from $43.84 (2022) to $57.23 (2023) and labor driving most of the claims-processing cost. (Premier) HFMA has reported initial denials nearing 12% in 2024 (Kodiak Solutions data). (HFMA) Experian’s 2025 State of Claims found 41% of providers say 10%+ of claims are denied. (Experian)
A second forcing function is workflow modernization in payer operations. The CMS Interoperability and Prior Authorization final rule (CMS-0057-F) introduces requirements beginning in 2026, including more standardized, electronic prior authorization and clearer denial reason requirements—making denial reasons more machine-parsable inputs for automated routing and corrective actions, if providers build the right intake pipelines. (Centers for Medicare & Medicaid Services)
Business impact: Agentic RCM is a cash and capacity lever—fewer touches per claim, faster denial turnaround, shorter A/R cycles. But the risk profile changes: autonomous actions must be contract-aware, policy-bound, and audit-ready, or you create fast, repeatable compliance failures. Winners will run agentic RCM as a governed production system, not a bot zoo.
CXO CTAs :
- Build an Autonomous Denials Loop for the top 10 denial reasons: classify → route root cause → retrieve evidence → draft appeal → submit → follow up, with one owner for the exception queue. (Experian)
- Make rework economics executive KPIs: cost-per-denial, first-pass yield, and preventable denial rate—so automation targets the highest-leverage failure modes. (Premier)
- Enforce autonomy boundaries + auditability: define what can execute end-to-end (status checks, evidence gathering, draft appeals) vs. what requires supervised approval (coding changes, medical necessity arguments, high-dollar claims), and log everything for dispute readiness.
Trend #17: AI-Native “Golden Paths” for Clinicians — tightened
Healthcare is rediscovering a basic truth: most clinical error, delay, and cost comes from workflow drift, not lack of knowledge. AI-native “golden paths” are the response—guided care flows that embed best practice into daily work so clinicians spend less time navigating steps and more time applying judgment. In 2026–2028, the shift is from CDS pop-ups to workflow-native guidance that reduces cognitive load, unwarranted variation, and in-basket chaos.
Why this trend exists:
- Workforce constraint: capacity is created by removing cognitive and administrative burden, not adding more alerts.
- Affordability shock: variation and rework become intolerable; golden paths operationalize standardization without turning medicine into checkbox care.
- Trust and liability: inconsistent execution across clinicians/units becomes reputational and safety risk.
What enables it now:
- Workflow telemetry is usable: event logs and process mining can show where orders, referrals, and follow-ups break—so the “happy path” can be engineered from reality, not policy binders. (sciencedirect.com)
- EHR task burden is measurable: evidence on “pajama time” reinforces that reducing clicks and routing friction is a capacity strategy. (jamanetwork.com)
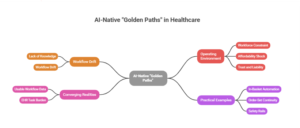
What golden paths look like (in practice):
- In-basket triage and auto-routing with clear ownership and closure rules
- Documentation → orders → follow-up scheduling executed as one guided flow
- Safety rails for missing prerequisites, contraindications, and discharge completeness
Business impact: Golden paths improve throughput by reducing rework and handoffs, improve quality by stabilizing execution, and improve retention by returning time. The failure mode is predictable: if paths feel imposed or misaligned, clinicians bypass them and create shadow workflows that undermine safety and measurement.
CXO CTAs:
- Pick 3 high-volume workflows (discharge, referral completion, abnormal result follow-up) and define measurable targets: completion rate, time-to-close, rework rate.
- Use process mining to design from reality: map actual steps and bottlenecks, then redesign handoffs and ownership. (sciencedirect.com)
- Govern golden paths like products: clinical + ops owners, monthly tuning cadence, and a logged override/exception policy that improves the system over time.
Trend #18: Modular / Domain-Specific Healthcare AI Platforms
Healthcare AI is standardizing around a hard-earned lesson: point solutions win the pilot, but they fragment the enterprise. In 2026–2028, the shift is toward modular, domain-specific AI platforms—a “model + tools + governance” layer that lets you assemble many fit-for-purpose capabilities (coding, triage, imaging, care management, denials, navigation) without rebuilding integration, evaluation, and controls every time.
McKinsey has been explicit about the direction of travel: healthcare AI is evolving away from scattered point solutions toward a modular, connected architecture that brings together point solutions, data infrastructure, and intelligent agents into a cohesive whole—because the real battleground becomes who controls the data and orchestration layers. (McKinsey & Company)
This is also why “one model everywhere” is dying. Gartner predicts that by 2027 organizations will use small, task-specific models at least 3× more (by volume) than general-purpose LLMs—exactly the pattern a modular platform enables (many domain-tuned models behind shared controls). (Gartner)
Why this trend exists now (healthcare-specific):
- Regulatory pressure is turning AI transparency into table stakes. ONC’s HTI-1 final rule establishes transparency requirements for predictive DSIs in certified health IT—pushing enterprises toward standardized documentation, monitoring, and governance patterns instead of ad hoc deployments. (ASTP)
- Operating reality demands reuse. Every new AI use case needs the same plumbing: identity/permissions, data access, audit trails, evaluation, monitoring, escalation. Platforms win because they make that reusable. HIMSS guidance emphasizes governance-first, minimum standards, and safe deployment muscle—exactly what platforms institutionalize. (HIMSS)
Business impact: A modular platform cuts time-to-production, reduces integration duplication, improves auditability, and makes outcomes comparable across use cases. Without it, you get “AI sprawl”: duplicated connectors, inconsistent evaluation, permission drift, and no enterprise answer to “which model did what, where, and with what evidence.”
CXO CTAs:
- Build a Healthcare AI Platform Blueprint with 5 non-negotiables: model registry (“model garden”), tool/connector registry, evaluation harness, monitoring/incident response, and policy/governance gates. (McKinsey & Company)
- Mandate evidence-grade evaluation per domain (clinical, RCM, ops): baseline, safety metrics, drift monitoring, and rollback rules—aligned to HTI-1 transparency expectations where applicable. (ASTP)
- Standardize reusable connectors/tools (EHR/RCM/contact center/imaging/data platforms) so teams compose capabilities instead of rebuilding integrations. (McKinsey & Company)
- Adopt a federated operating model: central platform + governance, local domain ownership for workflow and outcomes—so autonomy doesn’t become chaos. (HIMSS)
- Plan for a many-model world: task-specific models where precision and cost matter, larger models where flexibility matters—managed through one platform control surface. (Gartner)
Trend #19: EHR-as-platform accelerates (AI + interop + ecosystems) — tightened
The EHR is no longer just the system of record. In 2026–2028 it becomes the distribution layer: where AI features are deployed, interoperability becomes operational, and third-party apps plug directly into workflow. The strategic shift is that value moves from standalone tools to capabilities delivered inside the EHR’s gravity well—because identity, context, orders, messaging, and clinical accountability already live there.
What’s converging to make this inevitable:
- Interoperability becomes a utility: TEFCA is positioned as a “universal floor” for exchange across proprietary boundaries, raising expectations that data follows the patient by default. (ASTP)
- App ecosystems standardize: SMART on FHIR enables substitutable apps inside workflow with SSO, scoped access, and repeatable integration patterns—visible in Epic’s on-FHIR ecosystem. (Epic on FHIR)
Why this trend exists now:
- Workforce constraint: if it isn’t in the workflow, it won’t scale—EHR-native wins by reducing context switching.
- Trust and auditability: permissions, provenance, and documentation controls are strongest in the EHR, so AI and automation gravitate there.
- Platform concentration: leverage increases, but so does systemic risk—EHR downtime becomes a board-level safety and continuity issue.
Business impact: EHR-as-platform compresses time-to-adoption and raises the ROI ceiling because capabilities land where clinicians already work. The failure mode is equally clear: without platform governance you get app sprawl, inconsistent permissions, brittle integrations, and amplified downtime blast radius—because the EHR becomes the choke point for both productivity and safety.
CXO CTAs:
- Run the EHR like a platform product: roadmap + SLAs for workflow-native AI, app onboarding, interoperability uptime/versioning, and clear ownership. (ASTP)
- Standardize integrations on SMART on FHIR patterns (SSO, scopes, auditability) to avoid bespoke interfaces and uncontrolled access. (Epic on FHIR)
- Build ecosystem governance + resilience: approved app registry, security/clinical safety review, post-go-live monitoring, and downtime engineering (read-only modes, drills, recovery).
Trend #20: Epic Systems: “Cosmos” & Evidence-Based Scale (“Health Brain”)
The strategic shift is that de-identified longitudinal data is moving from “research asset” to point-of-care leverage. Cosmos isn’t just a big dataset; it’s a mechanism for turning population-scale longitudinal experience into “patients like this” evidence that can inform care decisions, operational predictions, and AI guardrails inside workflow.
Cosmos is now at a scale where it changes what’s practical: Epic positions Cosmos at roughly 300M patients and 18.3B encounters, with tools designed to bring insights back to clinicians at the point of care. (Epic Cosmos) This scale is also showing up in published research and model development: a 2025 Microsoft Research publication describes using Epic Cosmos for large-scale medical event modeling across 300M unique patient records and 16.3B encounters, illustrating how these longitudinal event streams can power foundation-style models in healthcare. (Microsoft)
Why this trend exists now:
- Evidence is becoming operational. Epic explicitly frames “Cosmos powers tools at the point of care,” signaling the shift from retrospective analytics to embedded insight loops. (Epic Cosmos)
- AI needs guardrails that aren’t just policy. At this scale, real-world outcomes can be used to validate or challenge AI suggestions (“does the data line up?”), turning evidence into a safety control rather than an academic exercise. (Healthcare IT Today)
- Healthcare needs longitudinal truth, not claim snapshots. Epic emphasizes Cosmos includes richer clinical data than claims alone (e.g., vitals and social drivers), which matters for nuanced cohort matching and risk prediction. (Epic Cosmos)
Business impact: Cosmos-like evidence scale changes competitive advantage for AMCs and large providers: faster cohort discovery, more credible real-world evidence (RWE), better operational predictions, and the potential to embed “what happens next” intelligence into workflows. Epic’s own “Curiosity” positioning underscores this direction—predictive insights learned from very large volumes of patient events to estimate risk, LOS, and outcomes. (Epic) The risk is equally material: if governance, de-identification discipline, and clinical applicability aren’t handled rigorously, “health brain” becomes a trust and reputation liability.
CXO CTAs:
- Treat evidence-at-scale as a product, not a database: define priority use cases (cohort discovery, risk stratification, therapy outcomes, operational forecasting) and measure impact in clinical and financial terms. (Epic Cosmos)
- Create an “evidence-to-workflow” governance path: what insights can influence decisions, what requires clinician confirmation, and what must be blocked until validated locally.
- Use Cosmos/RWE as an AI safety rail: require any high-impact AI recommendation to be explainable against observed real-world patterns (and flag when it conflicts). (Healthcare IT Today)
- Put privacy and trust posture on rails: standardized de-identification expectations, access controls, and auditability across research and operational use. (Epic Cosmos)
Trend #21: Enterprise Data Platforms and “Interoperability as Utility”
Interoperability is moving from “integration projects” to a managed utility—with uptime, versioning, security, and clear product ownership. In 2026–2028, winners will treat exchange like critical infrastructure: operated, not implemented. The shift is from interface sprawl to a platform discipline: APIs + semantics + consent/identity + operations—because prior auth, care transitions, and longitudinal risk can’t scale on brittle point-to-point integrations.
What makes this non-optional:
- TEFCA is hardening the national exchange rail via QHIN-to-QHIN connectivity, raising expectations that clinical data can move across networks under a common agreement.
- CMS-0057-F makes administrative interoperability real: impacted payers must implement FHIR-based APIs (Provider Access, Patient Access, Prior Authorization, Payer-to-Payer) and modernize electronic prior auth—turning “admin interop” into dated, reportable operational work. (Centers for Medicare & Medicaid Services)
That’s why the center of gravity shifts to enterprise data platforms: you need a data + API product layer and a semantic discipline that makes exchanged data usable—not just transferable—with an operating model that can answer: what version is live, what changed, what broke, and who owns the contract.
Where the market is standardizing:
- HL7 Da Vinci implementation guides—especially Prior Authorization Support (PAS)—are formalizing EHR ↔ payer workflows to replace fax/phone loops. (HL7)
- Payers/providers are being pushed into shared exchange mechanics and measurable operational performance, making interoperability an KPI, not an IT milestone. (Centers for Medicare & Medicaid Services)
Business impact: Interoperability-as-utility reduces friction where healthcare bleeds money: eligibility confusion, prior auth delays, missing context at transitions, and duplicative tests. The failure mode is interop debt—API drift, broken mappings, consent ambiguity, and “unknown ownership” outages that ripple across care and revenue cycles.
CXO CTAs:
- Stand up an Interoperability Product function (GM + roadmap + SLAs): uptime, versioning, change control, partner onboarding, incident response—run it like critical infrastructure. (Centers for Medicare & Medicaid Services)
- Prioritize admin interoperability now (eligibility, prior auth, payer-to-payer): align to CMS-0057-F requirements and operational reporting so it reduces cost, not just meets compliance. (Centers for Medicare & Medicaid Services)
- Standardize the rails and the meaning: adopt HL7 Da Vinci (PAS) patterns and enforce a semantic + consent/identity layer so exchange is usable, auditable, and resilient—not just “data flowing.” (HL7)
Trend #22: Real-world data at scale becomes a strategic asset — tightened
Real-world data (RWD) is shifting from “analytics support” to economic leverage. In 2026–2028, real-world evidence (RWE) becomes continuous and operational: it drives market access, defends pricing, enables outcomes-based contracts, and de-risks regulatory commitments. The competition is moving from who has data to who can produce credible, repeatable, audit-ready evidence fast. (U.S. Food and Drug Administration)
This is becoming structural because the bar for “good evidence” outside randomized trials is rising:
- FDA continues to formalize how RWE is evaluated and used as clinical evidence derived from RWD. (U.S. Food and Drug Administration)
- CMS Coverage with Evidence Development (CED) guidance is tightening expectations for study design and execution using RWD—making coverage increasingly contingent on credible evidence operations. (Centers for Medicare & Medicaid Services)
- Outcomes-based contracting doesn’t scale without shared endpoints, dependable pipelines, and governance that withstands payer scrutiny. (ISPOR)
What changes operationally: RWE stops being a research function and becomes an evidence factory with product-like SLAs:
- stable, explainable cohort definitions
- endpoints mapped to coverage/contract terms
- rapid-cycle measurement (months, not years)
- audit trails from raw data → analysis → decision
Business impact:
- Faster, more defensible coverage and formulary positioning when evidence is contract-ready, not publication-ready. (ISPOR)
- Pricing defense improves when real-world effectiveness and utilization become negotiating currency. (chiefhealthcareexecutive.com)
- Lower risk when post-market confirmation can be run continuously and credibly. (Reuters)
- Less duplicated wrangling and fewer one-off studies as pipelines become reusable infrastructure.
CXO CTAs (3):
- Stand up an Evidence-to-Contract operating model: one owner accountable for turning RWD into payer-ready endpoints with cycle-time SLAs and auditability. (ISPOR)
- Standardize methods and governance: payer-aligned RWE standards (bias handling, endpoint validity, transparency) plus provenance/reproducibility/change control so evidence survives scrutiny. (jmcp.org)
- Pre-wire CED readiness where needed: protocol templates, data access, governance, and study ops built before launch for products likely to face “coverage with evidence” expectations. (Centers for Medicare & Medicaid Services)
Trend #23: AI-Accelerated Discovery, Trials & Research Ops
AI is compressing the biopharma clock—but not uniformly. In 2026–2028, the winners won’t be the teams with the flashiest discovery demos; they’ll be the ones that industrialize AI across the full R&D operating system: target discovery → candidate design → biomarker strategy → protocol design → site selection → recruitment → monitoring → data cleaning → submission assembly. The unit of advantage shifts from “better models” to faster, more reliable cycle time under credibility and regulatory expectations.
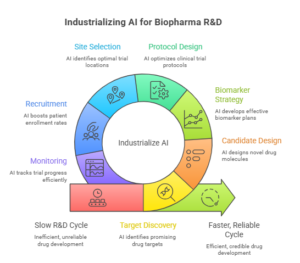
Two realities define the moment:
- Regulators are leaning in—but demanding credibility. FDA has explicitly acknowledged increased AI use across the drug product lifecycle and has published guidance on using AI to support regulatory decision-making, emphasizing risk-based credibility assessment tied to context of use. (U.S. Food and Drug Administration)
- Operational AI is paying where trials get stuck. McKinsey’s analysis of operational AI/ML pilots suggests AI can help identify optimal sites, boost enrollment, and predict enrollment performance—i.e., the value is often in trial execution, not just molecule ideation. (McKinsey & Company)
What’s already happening in the market (signals, not hype):
- FDA is qualifying AI tools that standardize endpoints. In December 2025, FDA qualified AIM-NASH—an AI tool that evaluates liver biopsy images to help speed drug development for MASH by standardizing assessments that are otherwise manual and inconsistent. (Reuters)
- Discovery-to-clinic is still hard. Reuters reported in January 2026 that Isomorphic Labs pushed its first clinical trials timeline to end-2026—useful as a reminder that AI can accelerate early steps, but translational and clinical realities still dominate timelines. (Reuters)
- Big-ticket partnerships are proliferating, with mixed expectations. The Financial Times covered AstraZeneca’s AI partnership dealmaking while noting persistent skepticism and the need for better benchmarking of AI value. (Financial Times)
Business impact: AI can reduce cycle time and cost by improving feasibility, enrollment, monitoring, and data quality—often delivering earlier value than “moonshot” discovery. But it also raises a new gating constraint: proof of credibility, traceability, and reproducibility. If you can’t defend model behavior and data lineage, you’ll either fail regulatory confidence tests or stall in internal governance.
CXO CTAs:
- Treat AI as an R&D throughput program, not a data science program: pick 2–3 bottlenecks (site selection, enrollment acceleration, eligibility screening, data cleaning) and measure cycle-time impact end-to-end. (McKinsey & Company)
- Build an AI credibility playbook aligned to FDA expectations: context-of-use definitions, validation approach, drift monitoring, and documentation that is submission-ready. (U.S. Food and Drug Administration)
- Prioritize “endpoint industrialization” where variability is costly: pathology/imaging scoring, adjudication support, and standardized biomarker readouts (AIM-NASH is the archetype). (Reuters)
- Install benchmarking discipline: require every AI use case to beat a baseline on speed, quality, and cost—otherwise partnerships and pilots become expensive theater. (Financial Times)
- Build a translation reality check: create a stage gate that explicitly tests whether AI-generated candidates are likely to survive preclinical/CMC/clinical constraints—so timelines don’t get “discovered” late. (Reuters)
Trend #24: Precision medicine industrializes (genomics + imaging + pathology into workflows) — tightened
Precision medicine is moving from “specialty center excellence” to industrialized standard of care—but only where it’s embedded into ordering pathways, diagnostic operations, and treatment governance. In 2026–2028, the differentiator won’t be who has sequencing or AI pilots; it will be who can run repeatable, equitable, turnaround-time reliable precision workflows that clinicians actually use.
What’s pushing this into an operating model:
- Companion diagnostics (CDx) are now gating mechanisms for therapy; FDA defines CDx as essential for safe and effective use and maintains an active list of cleared/approved devices (including imaging tools). (U.S. Food and Drug Administration)
- Digital pathology is industrializing (workflow integration, consolidation, regulatory maturity), making pathology + AI a dependable clinical lane—not a lab experiment. (DeciBio)
Why this trend exists now:
- Therapy complexity (especially oncology) is expanding biomarker-directed care into earlier lines and stages, making “who gets tested, when, and how” a pathway decision—not a specialist preference. (NCCN)
- Reimbursement is aligning with scale: reporting in January 2026 highlighted CMS reimbursement for an FDA-approved comprehensive genomic profiling test effective Jan 1, 2026, signaling that broader testing can be made practical when coded and positioned correctly. (Pathology News)
- Multimodal AI is accelerating integration of genomics + imaging + pathology into usable stratification and treatment protocols. (PMC)
Business impact: Industrialized precision medicine improves therapy selection, reduces ineffective treatment, tightens utilization, and enables scalable real-world evidence generation. The failure mode is predictable: inconsistent ordering, unreliable turnaround time, and results that land as PDFs without clear next steps—creating inequity, waste, and clinician mistrust.
CXO CTAs :
- Build precision ordering pathways (not “test availability”): qualification rules, panel/reflex logic, target turnaround times, and how results map to treatment decisions—anchored to guidelines/compendia. (NCCN)
- Industrialize diagnostics operations: specimen routing, digital pathology workflows, QC gates, and standardized reporting so precision is reliable at scale. (DeciBio)
- Make precision actionable and equitable: embed interpretation and next steps into workflow, and monitor testing rates/turnaround/treatment alignment by site and population to enforce “precision equity.” (PMC)
Trend #25: Pharmacovigilance shifts to real-time safety intelligence (RWD-driven)
Pharmacovigilance is moving from periodic, manual “case processing + quarterly reviews” to continuous safety intelligence: automated intake/triage, near-real-time signal detection, and faster benefit–risk action. In 2026–2028, safety becomes an operating system—measured by detection speed, investigation throughput, and audit-ready traceability—not just compliance outputs.
What’s driving it:
- Active surveillance is now table stakes: FDA’s Sentinel uses large-scale real-world data to monitor safety beyond spontaneous reports. (https://www.fda.gov/safety/fdas-sentinel-initiative)
- Signal management is industrializing: EMA’s model treats EudraVigilance as a core detection and assessment rail tied to ongoing benefit–risk review (via PRAC). (https://www.ema.europa.eu/en/human-regulatory/overview/pharmacovigilance/signal-management)
What changes operationally (PV “factory line”):
- ICSR (Individual Case Safety Report) processing becomes automation-first (intake → triage → de-dup → extraction/coding), with humans supervising exceptions and medical judgment—explicitly discussed in CIOMS’ draft on AI in PV. (https://cioms.ch/publications/product/cioms-ai-in-pharmacovigilance-draft-report/)
- E2B(R3) hardens the data pipe: structured electronic reporting makes automation easier—but punishes poor data quality and inconsistent semantics. (https://www.ich.org/page/e2b-implementation-guides)
Business impact: Real-time PV reduces the “latency tax” of safety: faster signal detection, quicker label/risk actions, lower rework in case processing, and stronger inspection readiness because traceability is engineered (not reconstructed). The failure mode is equally clear: automation without governance creates fast, repeatable errors—misclassified cases, missed signals, and weak audit trails that surface during inspections or safety events.
CXO CTAs:
- Stand up a Safety Intelligence Control Tower: one view of case inflow, processing SLAs, signal pipeline status, and escalation decisions—run weekly with named owners.
- Automate the front half first: intake → triage → dedup → coding → medical-review routing, with measured precision/recall and an exception queue owned by Safety Ops.
- Make traceability non-negotiable: enforce E2B(R3) data quality + semantics, expand beyond spontaneous reports using RWD signal workflows, and ensure every safety action is reproducible end-to-end.
Trend #26: Market access becomes a core capability (evidence + pricing defense)
In 2026–2028, market access stops being a downstream “commercial function” and becomes a core enterprise capability—because policy now changes economics, not just compliance. The shift is from launch planning to evidence-to-access operations: continuous proof generation, faster payer readiness, IRA-aware lifecycle strategy, and tighter control of pricing and affordability narratives.
Two policy rails are forcing this into the operating model:
- Part D redesign changes who pays what and when, reshaping net price dynamics and contracting incentives across plans, manufacturers, and beneficiaries. CMS (Centers for Medicare & Medicaid Services) issued Final CY 2026 Part D Redesign Program Instructions to guide IRA-driven changes to the defined standard Part D benefit. (Centers for Medicare & Medicaid Services)
- Medicare Drug Price Negotiation is now a repeating cycle, and the third round (for price applicability year 2028) was just triggered with 15 new drugs selected and negotiations occurring in 2026. That means “access strategy” must anticipate negotiation risk years before loss of exclusivity. (Centers for Medicare & Medicaid Services)
This is why access becomes operational: evidence must be produced in the format payers and CMS (Centers for Medicare & Medicaid Services) can act on, and pricing strategy must be defensible under scrutiny and negotiation frameworks—continuously, not at launch.
Business impact:
- Revenue realization: faster, cleaner coverage decisions when evidence is contract-ready (endpoints, comparators, subpopulations) rather than publication-ready.
- Pricing defense: IRA negotiation risk becomes a lifecycle constraint that influences indication sequencing, contracting posture, and post-market evidence priorities. (Centers for Medicare & Medicaid Services)
- Risk and resilience: failure modes (slow evidence, weak comparators, poor affordability posture) now translate directly into access barriers and margin compression—often with public visibility.
CXO CTAs:
- Stand up an Evidence-to-Access pipeline: one accountable owner for turning RWD/RWE + HEOR into payer-ready endpoints with cycle-time SLAs (not “study completion” milestones).
- Build an IRA-aware lifecycle playbook: model negotiation exposure early, pre-wire the evidence you’ll need for coverage defense, and design contracting and patient affordability posture to survive scrutiny. (Centers for Medicare & Medicaid Services)
- Treat Part D redesign as contracting strategy, not policy noise: update gross-to-net assumptions, discount architecture, and patient cost-sharing implications under the 2026 guidance. (Centers for Medicare & Medicaid Services)
- Create a Market Access Control Tower across Medical, HEOR, Legal/Compliance, Pricing, and Government Affairs—because policy cadence now moves faster than annual brand planning. (Centers for Medicare & Medicaid Services)
- Stress-test “affordability and trust” messaging: access is increasingly influenced by how credible your affordability narrative is under regulator, employer, and payer lenses (and how it holds up when negotiation is on the table). (zs.com)
Trend #27: Sovereign & Disconnected Data Clouds + Privacy-Preserving and Quantum-Resilient Health Data Strategies
Health data has a long half-life. PHI and genomics can remain sensitive for decades—so the 2026–2028 shift is toward architectures that assume jurisdictional constraints, selective disconnection, and cryptographic transition planning. The winners won’t be the orgs with the “most cloud.” They’ll be the orgs that can collaborate and compute on sensitive data without moving it, and can prove data locality, operator access controls, and survivability under changing regulation.
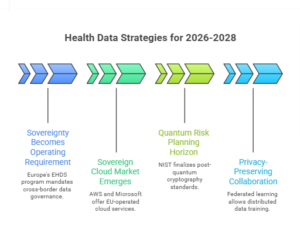
Three forces are converging:
- Sovereignty becomes an operating requirement, not a preference. Europe’s EHDS program is explicitly building a cross-border health data framework with governance for both primary use and secondary use, pushing enterprises toward tighter controls on access, interoperability requirements, and compliance posture. (Public Health)
- “Sovereign cloud” is becoming a real market construct. AWS has publicly framed its European Sovereign Cloud as EU-operated (including EU-citizen staffing for operational roles), reflecting how deep sovereignty requirements can go beyond “region selection.” (IT Pro) Microsoft is also expanding in-country processing and sovereignty options, signaling that major platforms are productizing locality and operational boundaries—not just storage location. (TechRadar)
- Quantum risk is now a planning horizon issue. NIST finalized its first post-quantum cryptography standards (including ML-KEM and signature standards), which effectively starts the clock on migration planning for long-lived sensitive datasets. (NIST)
The less obvious but decisive technical shift: privacy-preserving collaboration becomes practical. Federated learning and related privacy techniques allow institutions to train models across distributed data without pooling raw datasets—while also introducing new threat models that must be governed (inference leakage, trust between parties, secure aggregation). (ScienceDirect)
Business impact:
- Speed + resilience: you can collaborate (research, safety, population insights) without negotiating raw data movement every time—reducing cycle time and legal friction. (ScienceDirect)
- Risk + trust: sovereignty, operator access, and selective disconnection reduce blast radius from cyber events and third-party concentration risk—especially for genomics and “crown jewel” datasets.
- Cost: this adds complexity (multiple zones, enclaves, controls), but it avoids existential risks (regulatory breach, cross-border injunctions, or “replatform under duress”). (Reuters)
CXO CTAs:
- Define a data criticality tiering model (PHI, genomics, research, operational telemetry) and map each tier to an architecture: sovereign, restricted, standard, and disconnected vault—so locality and disconnection are intentional, not accidental.
- Stand up a sovereignty assurance pack: where data resides, who can operate systems, what support access exists, and how access is logged and audited—because sovereignty increasingly includes operations, not just geography. (IT Pro)
- Build privacy-preserving collaboration rails (clean-room patterns, federated learning, secure aggregation) for the top 2–3 cross-institution use cases (e.g., rare disease cohorts, imaging/pathology model training, multi-site outcomes studies), with explicit leakage testing and governance. (ScienceDirect)
- Start selective post-quantum planning now for long-lived sensitive stores: crypto inventory, “where signatures matter,” migration pilots, and vendor roadmaps—prioritize crown jewels instead of boiling the ocean. (NIST)
- Run a disconnected-mode exercise for critical workflows and datasets (what must still operate when connectivity is constrained), and ensure the data strategy aligns with resilience engineering—not just compliance.
Trend #28: Cyber-Physical Resilience (“Survival Servers”) + cyber resilience engineering
Healthcare is moving from cybersecurity as “prevent breaches” to cyber resilience as continue care during failure. In 2026–2028, the new baseline is bunker-mode capability: contain, recover, and keep core clinical operations running even when the cloud, the network, or a major vendor is down. This is not an IT maturity choice—it’s patient safety engineering.
The shift is being forced by two realities:
- Outage and ransomware blast radius now hits clinical operations directly. KLAS has documented that healthcare increasingly expects vendors to prove security capability and resilience posture, because third-party dependency and ecosystem concentration amplify operational risk. (klasresearch.com)
- Attack trends are evolving into “extortion + disruption,” not just data theft. Industry reporting notes a continued high threat environment and emphasizes resilience, downtime planning, and recovery preparedness as core defenses. (hhs.gov)
What “survival servers” means in practice isn’t a return to old on-prem. It’s architected continuity:
- segmented networks so compromise doesn’t propagate
- immutable backups with tested restores
- predefined clinical downtime workflows (med admin, labs, imaging, orders, patient identity)
- controlled third-party access (least privilege, just-in-time, monitored sessions)
- planned degraded modes for critical systems
The macro driver is also market pressure: outages and cyber events can damage contracting leverage and brand trust fast—especially when patient care is visibly disrupted.
Business impact:
- Clinical safety: reduced harm during outages (med errors, delays, lost results).
- Financial resilience: shorter downtime = lower revenue loss, lower remediation cost, lower payer/provider dispute friction.
- Trust as capital: better post-incident credibility with regulators, partners, and patients. The failure mode is “paper plan resilience”: policies and runbooks that are not rehearsed, backups that don’t restore, and vendor access that becomes the compromise vector.
CXO CTAs:
- Build a Bunker-Mode Minimum Viable Hospital: define the smallest set of capabilities that must continue for 72 hours (identity, meds, labs, imaging access, orders, discharge essentials) and engineer systems and workflows to support it.
- Run recovery drills like clinical simulations: quarterly restore tests, downtime exercises with clinicians, measured time-to-recover targets, and after-action remediation.
- Segment and contain: treat network segmentation and privileged access controls as patient safety architecture, not “security projects.” (hhs.gov)
- Map third-party blast radius: inventory critical vendors, enforce just-in-time access, and require evidence of resilience posture—not checklists. (klasresearch.com)
- Establish a board-visible Resilience Scorecard: recovery time objectives achieved, drill performance, critical patch cadence, third-party access incidents, and downtime event frequency.
Trend #29: Proof-Based AI Governance (“Show the Evidence or Switch It Off”)
In 2026–2028, AI in healthcare stops being governed like software and starts being governed like a clinical product and a financial control. The shift is from “we approved a model” to “we can continuously prove it is safe, effective, compliant, and worth it—in our environment—and we can shut it off fast when it isn’t.”
This is no longer optional because regulation is converging with operational risk:
- ONC’s HTI-1 Final Rule introduces first-of-its-kind transparency requirements for predictive algorithms used in certified health IT—meaning organizations need the ability to produce model facts, limitations, and user-facing transparency as a repeatable discipline, not a one-time vendor document. (ASTP)
- FDA is formalizing credibility expectations for AI used to generate information supporting regulatory decision-making, using a risk-based credibility assessment tied to context of use. That same “credibility-by-context” logic is now bleeding into how boards and clinicians expect AI to be governed, even outside regulated submissions. (U.S. Food and Drug Administration)
- NIST AI RMF 1.0 has become the de facto playbook for lifecycle risk management (govern, map, measure, manage)—and it’s increasingly the common language auditors, regulators, and enterprise risk teams use to evaluate AI posture. (NIST Publications)
What changes operationally: governance becomes proof machinery, not policy.
- Pre-deployment evaluation (bias, safety, performance vs baseline, failure modes)
- In-production monitoring (drift, error leakage, calibration, subgroup performance)
- Escalation and accountability (who owns incidents, who can pause/rollback)
- Audit trails (what the model saw, what it output, what action was taken)
- Transparency artifacts (what it is, what it isn’t, intended use, known limitations)
The key design point: healthcare needs kill switches with criteria. “Human in the loop” is not governance unless you define when humans must intervene, what gets logged, and what thresholds trigger shutdown.
Business impact: Proof-based governance is how you unlock scale without betting the enterprise’s reputation. It reduces clinical risk, reduces regulatory and liability exposure, and prevents “AI sprawl” by forcing every deployment to earn the right to exist with evidence. The counterfactual is expensive and familiar: pilots that look good, then stall—or worse, scale until an incident forces a public rollback.
CXO CTAs:
- Establish a single AI safety & value bar across clinical + admin use cases: baseline comparison, minimum acceptable performance, subgroup checks, and documented intended use aligned to HTI-1 transparency expectations. (ASTP)
- Implement continuous monitoring + escalation as production requirement: drift, error leakage, “near miss” reporting, and a standing review cadence that can tighten policies monthly. (NIST Publications)
- Require context-of-use credibility for any high-impact model (diagnosis support, triage, utilization decisions): validation evidence and limitations must match real workflow and population—not vendor benchmarks. (U.S. Food and Drug Administration)
- Create kill-switch governance: pre-defined shutdown triggers, rollback paths, and a named incident commander—because “we’ll fix it next release” is not acceptable in clinical workflows.
- Put governance where work happens: embed transparency and “why” into the UI, not in a PDF policy binder—so the clinician/operator can understand limits at decision time. (ASTP)
Trend #30: Workforce “Gigification” Platforms
Healthcare’s workforce constraint won’t be solved by hiring; it will be solved by capacity routing. In 2026–2028, leading systems will run internal labor like a marketplace: dynamically matching shifts, skills, credentials, and census demand across units and sites—reducing reliance on expensive agency staffing and smoothing throughput bottlenecks.
The shift is from “staffing as scheduling” to staffing as real-time operations:
- internal float pools become productized
- credentials and competencies are machine-checkable
- staffing is adjusted to census volatility, not monthly plans
- incentives and pay differentials are tuned to move capacity where the system needs it
Why this trend exists now:
- Persistent shortages and burnout: the pipeline isn’t refilling fast enough, and overtime/agency dependence is financially and culturally corrosive.
- Affordability shock: labor is often the largest cost line; variability in staffing efficiency becomes margin volatility.
- Operational telemetry has improved: real-time census, acuity scoring, and workload measures can now drive staffing decisions rather than gut feel.
Market signal examples:
- Internal float pools and marketplaces are scaling as systems try to reduce agency spend and improve retention; AMN Healthcare has documented how internal resource pools and float strategies are used to address staffing shortages and reduce contract labor dependence. (amnhealthcare.com)
- Technology platforms are emerging specifically for internal staffing, including real-time workforce management and credentialing automation, reflecting the shift from HR tooling to operational capacity tooling. (deloitte.com)
Business impact:
- Cost and efficiency: reduced premium labor (agency, overtime), better staffing utilization, fewer last-minute shift gaps.
- Speed and adaptability: faster response to census spikes and seasonal volatility.
- Risk and resilience: safer staffing levels and reduced burnout-driven attrition when workload is managed proactively.
- Experience: staff feel more agency and flexibility when internal gigs are transparent and accessible.
The failure mode is also clear: if gigification is just “Uber-for-nurses” without governance, it can degrade continuity, create resentment, and increase patient safety risk due to unfamiliarity and uneven competency matching.
CXO CTAs:
- Stand up an Internal Labor Marketplace with three foundations: verified credentialing/competencies, transparent shift supply/demand, and incentive levers that can move capacity within hours—not weeks. (amnhealthcare.com)
- Treat staffing as a command-center capability: integrate census, acuity, and workload signals into staffing decisions with clear escalation rules.
- Build guardrails for continuity: define when gig staffing is allowed, minimum orientation requirements, and unit “familiarity thresholds” to protect safety.
- Shift measurement from “filled shifts” to outcomes: overtime rate, agency spend, nurse turnover, patient safety events, and throughput (boarding time, LOS).
- Align labor relations and culture: publish fairness rules for shift access and differentials so marketplace flexibility doesn’t become a trust problem.
Trend #31: Systemic Mental Health & the “Loneliness” Metric
Mental health is shifting from episodic crisis response to a longitudinal operating metric—and “loneliness / social isolation” is emerging as a measurable driver of cost, utilization, and outcomes. In 2026–2028, leading payers and providers will treat social connection as a health risk factor with interventions, not a soft community issue.
The framing is now mainstream public health. The U.S. Surgeon General elevated loneliness and social isolation as a major health concern, citing associations with increased risk of premature death and multiple chronic conditions. (HHS.gov) CDC similarly documents that social isolation and loneliness increase risk for heart disease, stroke, depression/anxiety, dementia, suicidality/self-harm, and earlier death—making this a cross-cutting medical + behavioral driver, not just a behavioral health topic. (CDC) Globally, WHO’s Commission on Social Connection reports scale (about 1 in 6 people experiencing loneliness) and calls for treating social connection with the same urgency as physical and mental health. (who.int)
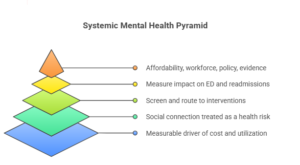
The shift: “mental health + loneliness” becomes a risk stratification and care model problem:
- Screen and track like a vital sign (especially in Medicare, chronic care, and post-acute transitions).
- Route to interventions that actually move outcomes (integrated behavioral health, care management, community programs, “social prescriptions”).
- Measure downstream impact (avoidable ED, readmissions, medication adherence, total cost).
Why this trend exists now:
- Affordability shock: loneliness drives avoidable utilization and worsens chronic disease management—meaning it’s a cost driver, not just a wellbeing issue. (CDC)
- Workforce constraint: you can’t scale clinician time for every need; you must operationalize triage + community-based support.
- Policy direction: CMS(Centers for Medicare & Medicaid Services) is explicitly elevating Social Drivers of Health and health-related social needs as part of innovation and care transformation—pushing the ecosystem toward more systematic identification and intervention. (Centers for Medicare & Medicaid Services)
- Evidence base is tightening: CDC surveillance and peer-reviewed work is making loneliness measurable and segmentable (by population, risk factors, outcomes), which enables payer/provider accountability. (CDC)
Business impact:
- Cost & efficiency: reduced avoidable ED and readmissions when high-risk members get targeted behavioral + social support (not just referrals). (CDC)
- Speed & adaptability: better transitions of care and fewer “bounce-backs” when loneliness and support deficits are identified early. (CDC)
- Risk & trust: brands and boards increasingly get judged on equity and access—ignoring social disconnection looks like neglect, not neutrality. (who.int)
CXO CTAs:
- Make loneliness / social connection a tracked risk indicator in your population health stack (screening + segmentation + trend reporting), not a one-off survey. (CDC)
- Operationalize “social prescriptions” as a real workflow: referral pathways, partner network SLAs, closed-loop follow-up, and outcome measurement. (Centers for Medicare & Medicaid Services)
- Integrate behavioral health into primary care pathways (warm handoffs, shared care plans), with accountability for follow-through—not just access to a directory. (CDC)
- Put loneliness into transition-of-care protocols (post-discharge, new diagnosis, bereavement, new disability) as a preventable utilization driver. (HHS.gov)
- Track the business outcomes that matter: avoidable ED, readmissions, adherence, and total cost by “social connection risk tier,” and fund what works.
Anti-Patterns to Avoid
Anti-Pattern 1: “Pilot Proliferation” (100 demos, zero operating model)
Why it looks attractive: Low-risk experimentation, lots of internal excitement, easy to fund. Why it fails: Healthcare value shows up only when workflows change and exceptions are owned. Pilot sprawl creates fragmented integrations, inconsistent permissions, uneven safety standards, and no single answer to “who is accountable when it breaks.” You end up with AI theater and rising risk.
Anti-Pattern 2: “Cost Takeout Without Clinical/Operational Redesign”
Why it looks attractive: Immediate savings targets; finance-led initiatives feel controllable. Why it fails: Cutting cost without redesign increases variation, delays, and rework—raising avoidable utilization and staff burnout. The system “saves” money on paper and pays it back through LOS creep, denials, cancellations, and churn. Zero-based clinical costing only works when paired with standardization governance and workflow enforcement.
Anti-Pattern 3: “Platform Dependency as Strategy” (concentration without resilience)
Why it looks attractive: Faster rollout, fewer vendors, simpler procurement, “one throat to choke.” Why it fails: Concentration amplifies downtime and cyber blast radius. When the EHR, identity, and exchange rails are centralized without bunker-mode design, a single outage becomes a clinical safety event and a reputation event. Platform leverage must be paired with resilience engineering—or it becomes systemic fragility.
Far-Fetch but Plausible Trend to Watch
The “Autonomous Care Logistics Layer”
Why it seems unrealistic today: Healthcare’s last mile is messy: homes are uncontrolled environments, regulations vary, and liability is complex. What could make it real in 3–5 years: As hospital-at-home industrializes and specialty therapies become more time/temperature sensitive, logistics becomes clinical. The edge trend is semi-autonomous care logistics: coordinated fleets, smart parcels, device self-checks, and agent-run scheduling that dynamically re-plans based on vitals drift, supply constraints, and staffing availability—like an air-traffic-control system for home and ambulatory care. Early signals to monitor: payer reimbursement expansion for home-based acute models, tighter traceability requirements, and measurable improvements in failure-rate (missed visits, delayed meds, temperature excursions) from logistics modernization.
One Trend That May Slow Progress
Trust & Liability Friction Outpacing Deployment Discipline
Even when the tech works, adoption can stall if clinicians, regulators, and patients don’t believe it’s safe or fair. The counterforce isn’t “AI skepticism”—it’s unpriced liability and unclear accountability. If organizations can’t prove record integrity (ambient), decision provenance (clinical guidance), and action auditability (agents), they will intentionally slow deployment to avoid reputational and legal exposure. The result: slower value realization, more conservative autonomy levels, and heavier oversight costs.
Closing Perspective — All-Up CTA
Healthcare leaders should stop treating these trends as separate initiatives. GLP-1 economics, MA reset, payvidor discipline, specialty risk, distributed networks, logistics precision, ambient/agentic automation, interoperability utility, and resilience engineering are all expressions of one reality:
Healthcare is being re-platformed under affordability shock and trust risk.
What to stop doing:
- Stop funding “digital” as a collection of tools instead of an operating model.
- Stop scaling pilots without control planes, exception ownership, and measurable outcomes.
- Stop assuming platform concentration is simplification if resilience isn’t engineered.
What to commit to in the next 12 months:
- Pick 5–7 workflows that carry P&L and safety weight (MA Stars closure, denials, discharge, prior auth, referral completion, home orchestration, specialty pathway adherence) and redesign them around owned exceptions + outcome KPIs.
- Stand up utility operations for interoperability (admin + clinical) and bunker-mode continuity for core clinical services.
- Treat trust as an engineering discipline: proof-based governance, audit trails, consent, and rapid shutdown/rollback.
What must be re-architected, not optimized:
- Your operating layer: how work moves across people, systems, and partners—with accountability and telemetry.
- Your data layer: semantics, consent/identity, and evidence pipelines that support contracting and care.
- Your resilience layer: recovery and continuity as clinical safety, not IT readiness.
Enterprise-level CTA: Build a single executive-owned “Healthcare Operating System” program—where affordability, capacity, evidence, and trust are engineered together—and where every automation is judged by outcomes, auditability, and resilience, not novelty.

Leave a Reply