Securing the Data Nerve Center: Microsoft Purview’s Defense-in-Depth Framework

Strengthening Governance for the AI Enterprise
At Microsoft’s May 2025 governance and security update, one theme resonated across every session and hallway conversation — data trust is the new perimeter.
As AI systems scale and Fabric becomes the backbone of enterprise analytics, the question for most CXOs isn’t “Where is our data?” — it’s “Can we trust it?”
That question sits at the heart of Microsoft’s latest release: the Data Governance Security Best Practices for Microsoft Purview.
The guidance reframes Purview not just as a compliance tool, but as a security architecture for data governance — one that blends Azure networking, Microsoft Entra identity, and Defender intelligence into a single defense-in-depth model.
“In the AI era, trust isn’t a control — it’s an architecture. Microsoft’s framework shows how governance itself can become the defense perimeter.”
— Gaurav Agarwaal
 My Take: The Blueprint for Secure Governance
My Take: The Blueprint for Secure Governance
Over the past year, we’ve seen enterprises adopt Purview as the foundation for unified governance — but implementation maturity varies widely.
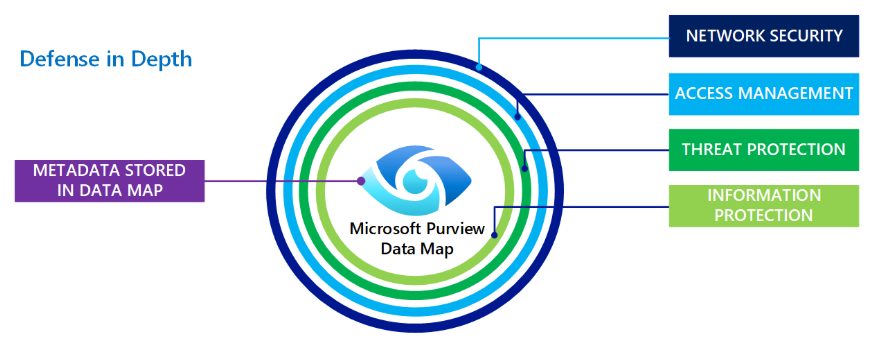
This new framework closes that gap. It breaks Purview’s protection strategy into seven practical layers that connect network isolation, identity, metadata protection, and operational resilience into a cohesive defense posture.
Here’s how each layer translates from policy to practice.
1. Network Isolation — Build Your Private Governance Perimeter
The first layer of defense is invisibility.
Microsoft’s latest network architecture for Purview demonstrates how end-to-end isolation creates a sealed governance boundary — where data traffic never leaves the private network.
At the heart of this design is Azure Firewall, connecting on-premises environments, Azure VNets, and Purview’s private endpoints under a unified security envelope.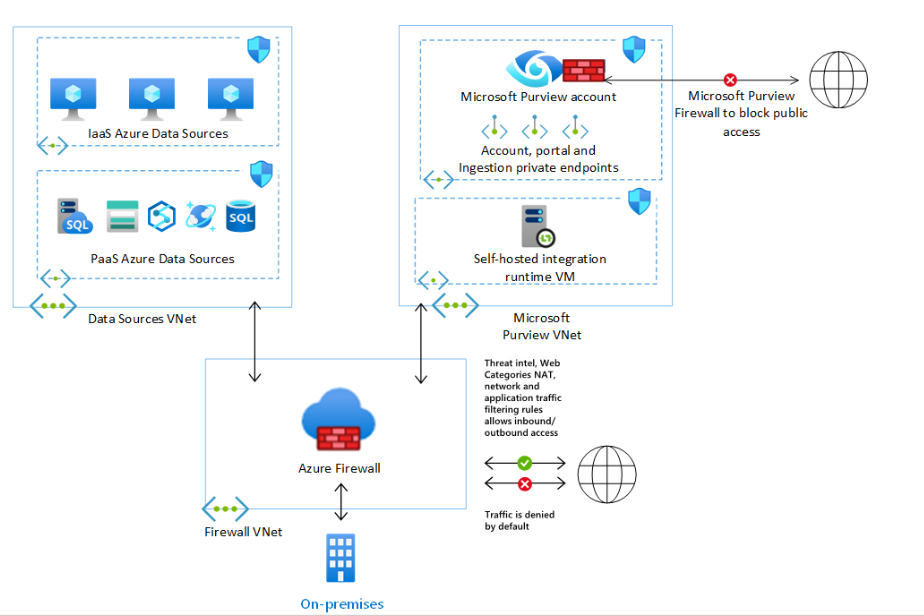
Here’s how it works in practice:
- Private Endpoints for Purview Accounts:
The Purview account, portal, and ingestion services are accessible only through private IPs inside a dedicated Purview VNet — ensuring all communication remains internal. - Microsoft Purview Firewall:
Public internet access is completely blocked, enforcing a private-only path for all governance and scanning operations. - Network Security Groups (NSGs):
Applied to subnets hosting Purview private endpoints and Self-Hosted Integration Runtime (SHIR) VMs, NSGs define strict inbound/outbound rules for metadata flow and scanning activity. - Azure Firewall as the Control Hub:
Positioned in a central Firewall VNet, it manages NAT, application rules, and threat-intelligence filtering between the Data Source VNet and the Purview VNet.
By default, all internet-bound traffic is denied unless explicitly allowed through defined rules. - On-Premises Integration:
Organizations connecting through VPN or ExpressRoute can securely extend their on-premises systems into the Purview boundary, maintaining private ingestion pipelines without exposing endpoints externally.
Result:
Purview becomes a sealed, policy-driven environment — invisible to the internet, auditable within your own perimeter, and monitored through a single firewall control plane.
“In every enterprise I’ve seen mature, isolation isn’t an afterthought — it’s the first sign of intent.”
— Gaurav Agarwaal
2. Identity & Access Management — Least Privilege by Design
Identity is the control plane of modern governance.
Purview’s layered access model separates deployment privileges from data interaction privileges, reducing risk and enforcing accountability.
Microsoft’s guidance:
- Assign roles to Microsoft Entra groups, not individual users.
- Use Access Packages to automate provisioning and revocation.
- Separate Control Plane roles (deployment, configuration) from Data Plane roles (catalog, scans).
- Enforce MFA and Conditional Access for privileged accounts — especially Admins, Curators, and Data Source Owners.
Example Role Segmentation:
| Plane | Typical Operations | Recommended Role Type |
| Control Plane | Deploy or delete Purview account, set up private endpoints | Azure RBAC (Contributor/Owner) |
| Data Plane | Create collections, run scans, manage lineage | Purview Roles (Collection Admin, Data Curator, Data Source Admin) |
Outcome: Every user’s access maps directly to purpose — a zero-trust governance posture in action.
“Least privilege isn’t a limiter — it’s the boundary that allows safe collaboration at scale.”
3. Credential Hygiene & Runtime Hardening — Secure the Connectors
If network isolation defines your perimeter, credential hygiene defines your integrity.
Every data connection in Purview — from a Fabric lakehouse to an on-premises SQL source — represents a potential risk boundary.
Microsoft’s framework emphasizes securing these connectors through hardened runtimes and identity-first authentication.
This architecture illustrates how Integration Runtimes (IRs) — whether managed or self-hosted — securely execute data movement and compute activities across trusted Azure regions.
Data Factory orchestrates metadata and pipelines, but all runtime executions happen in the same region as the compute or data source, ensuring that sensitive data never leaves its designated boundary.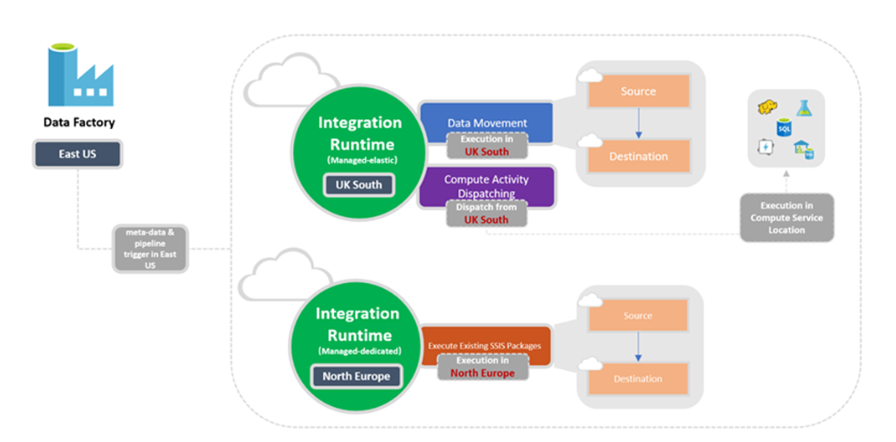
Microsoft’s Recommendations for Secure Connectors
- Use Managed Identities or Service Principals — never static credentials:
Each runtime authenticates through Azure AD, eliminating password-based connections and reducing credential sprawl. - Centralize Secret Management:
Store all keys and secrets in Azure Key Vault with Get/List permissions only. No credentials should ever live in code or configuration files. - Secure Self-Hosted Integration Runtimes (SHIRs):
- Apply Network Security Groups (NSGs) and Just-in-Time (JIT) access to limit inbound exposure.
- Enable Defender for Cloud for runtime-level threat detection and patch compliance.
- Keep SHIR virtual machines updated, isolated, and backed up.
- Use multiple SHIR nodes or VM scale sets for high availability and load balancing.
This layered approach ensures that metadata, credentials, and compute resources remain shielded — even as they interact across hybrid networks.
Practical Takeaway:
Treat each Integration Runtime as a governed infrastructure asset, not just a pipeline executor. It’s the bridge that connects your data gravity to the cloud — and that bridge must be continuously validated, monitored, and protected.
“The smallest credential misstep can undo the biggest governance program. Credential hygiene isn’t configuration — it’s culture.”
—Gaurav Agarwaal
4. Information Protection — Securing Metadata as an Asset
Purview doesn’t store your data, but the metadata it manages is equally sensitive.
The best practices redefine how that metadata is extracted, encrypted, and retained.
Microsoft’s approach:
- During scans, only metadata is collected — data never leaves its source.
- All metadata is stored in-region within the Purview Data Map.
- TLS 1.2+ encryption secures data in transit.
- Microsoft-managed keys encrypt data at rest.
- Key Vault integration ensures credentials and keys stay isolated.
Result: A model where security travels with metadata, not separate from it — enabling compliance that scales without friction.
“Governance maturity isn’t about how much data you control; it’s about how confidently you can describe it.”
5. Threat Protection — Align Security and Governance Intelligence
This is one of Microsoft’s most strategic integrations yet:
Purview now connects directly with Microsoft Defender for Cloud.
What this means:
- Purview’s sensitivity labels surface inside Defender, allowing correlation between data value and security posture.
- Defender recommendations now include secure score values tied to Purview assets.
- Alerts carry severity levels — helping security teams focus where business impact is highest.
https://www.youtube.com/watch?v=MV4gC8aVnh8&t=157s
Practical insight: This transforms data governance from a compliance function into a risk intelligence layer that informs enterprise security decisions.
“This integration bridges the gap between those who classify data and those who defend it. Finally, both teams are speaking the same language — risk.”
6. Automation — Turn Governance Into Continuous Assurance
Manual governance doesn’t scale.
Purview’s automation capabilities bring the discipline of DevOps into data security.
Microsoft’s best practices include:
- Automating metadata scans at defined intervals (hourly/daily/weekly).
- Using Azure Policy to continuously audit NSG configurations and access rules.
- Managing configurations via Azure CLI and PowerShell Purview Modules for repeatability.
- Leveraging Defender for Cloud alerts to trigger governance workflows automatically.
This automation turns governance from a static compliance task into a living, adaptive system.
“Automation isn’t the absence of control; it’s the guarantee of it.”
7. Operational Resilience — Planning for the Unexpected
Resilience completes the defense-in-depth strategy. Microsoft encourages enterprises to plan for disruption — because governance without continuity is just good documentation.
Key measures:
- Break-glass accounts: Maintain emergency admin access independent of conditional access policies.
- Resource Locks: Apply CanNotDelete or ReadOnly locks to critical Purview resources.
- Monitoring: Use Azure Monitor and Defender for Cloud for early anomaly detection.
- SHIR Resilience: Deploy multiple self-hosted runtimes to avoid single points of failure.
“Security without recovery is just risk deferred. True resilience blends readiness with restoration.”
What CXOs Should Do Next (Prescriptive)
- Eliminate public exposure. Move every Purview account behind Private Link.
- Unify identity controls. Integrate Entra access groups with MFA and conditional policies.
- Govern credentials like code. Automate key rotation and store secrets in Azure Key Vault.
- Correlate governance and security. Link Purview sensitivity insights to Defender for Cloud dashboards.
- Operationalize resilience. Test break-glass access quarterly; review NSG logs monthly.
Final Reflection: When Governance Becomes the Security Architecture
Microsoft’s 2025 security framework marks a philosophical shift — from treating governance as oversight to treating it as infrastructure.
By weaving network controls, Entra-based identity, encryption, and threat analytics into one connected model, Purview has become the trust layer for enterprise AI ecosystems.
“The future of governance isn’t about restricting access — it’s about orchestrating assurance.
When your data knows its own boundaries, trust becomes a built-in feature.”
— Gaurav Agarwaal

Leave a Reply